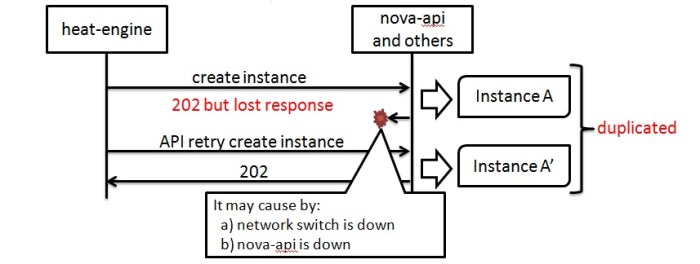
Idempotency in APIs: Definition, Benefits, and Best Practices
This comprehensive article delves into the critical concept of idempotency in APIs, explaining its fundamental definition and significance in ensuring...
175 posts in this category

This comprehensive article delves into the critical concept of idempotency in APIs, explaining its fundamental definition and significance in ensuring...
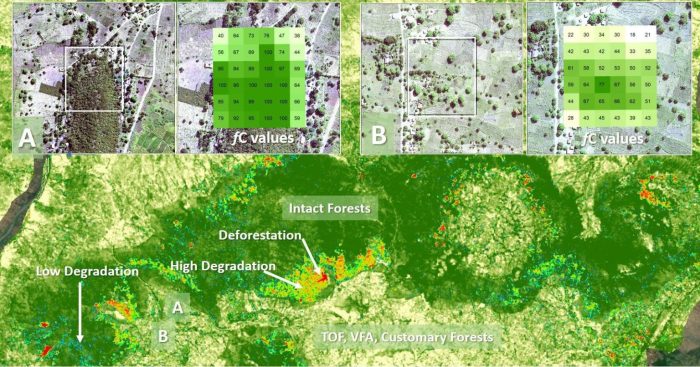
Large-scale message processing systems rely on effective strategies for handling high volumes and ensuring reliable delivery. The "Claim Check Patter...

Navigating the complexities of data in a cloud environment demands robust data governance. This article provides a comprehensive guide to implementing...

This comprehensive guide delves into the intricacies of designing a robust cloud data warehouse architecture, covering critical aspects from initial p...
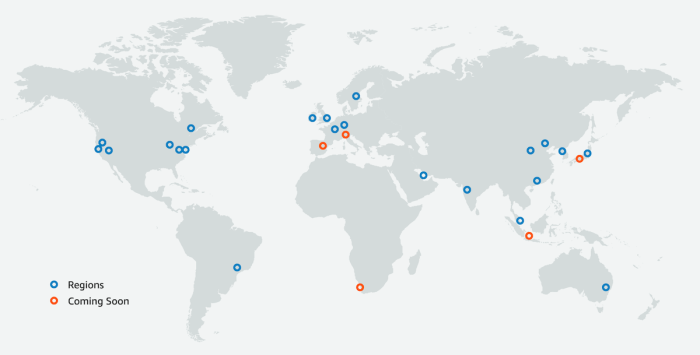
Understanding Availability Zones (AZs) is crucial for building resilient cloud applications. This article provides a comprehensive overview of AZs, ex...
Cloud architecture design, while offering great potential, is riddled with potential pitfalls that can undermine your cloud strategy. This article ide...
Operational excellence is paramount in cloud design, offering a comprehensive strategy for building and managing cloud environments. This approach pri...

This comprehensive guide explores the critical importance of rate limiting in distributed systems, covering everything from fundamental concepts and d...

This article provides a comprehensive overview of the Backends for Frontends (BFF) pattern, exploring its core concepts, benefits, and practical imple...

Hexagonal architecture leverages ports and adapters to isolate the core application logic from external concerns. This design pattern enhances softwar...

Edge computing is transforming data processing by minimizing latency and improving response times for real-time applications. By shifting computation...
Eventual consistency offers significant benefits for distributed systems but presents challenges for data integrity. This article explores the critica...