OAuth 2.0 and OpenID Connect: Secure Authentication Explained
This comprehensive guide delves into the intricacies of OAuth 2.0 and OpenID Connect, explaining their roles in modern authentication and authorizatio...
152 posts in this category

This comprehensive guide delves into the intricacies of OAuth 2.0 and OpenID Connect, explaining their roles in modern authentication and authorizatio...
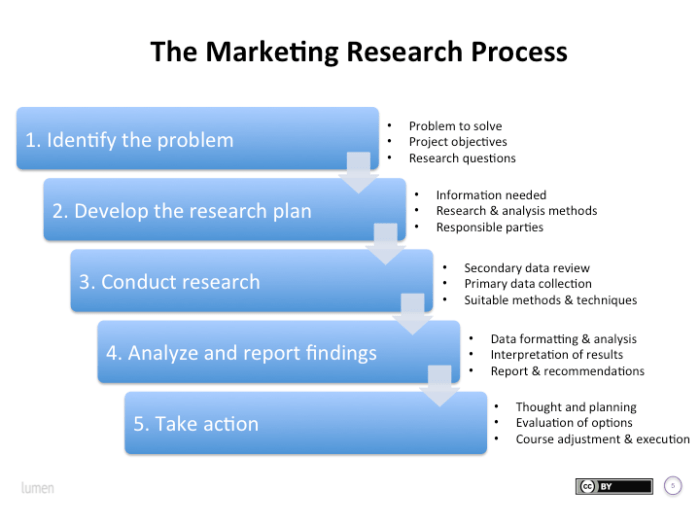
Want to strengthen your organization's digital defenses? This guide offers a comprehensive approach to conducting a security architecture review, prov...

Protecting sensitive data within big data platforms demands a comprehensive approach encompassing encryption, access control, data governance, and rob...

This comprehensive guide explores the multifaceted landscape of container security, outlining critical best practices to protect your deployments from...
In an increasingly cloud-dependent business environment, establishing a strong cloud security team is crucial for protecting valuable data and applica...
Configuration drift in security settings poses a significant threat, potentially weakening your defenses through unnoticed changes. Proactively monito...
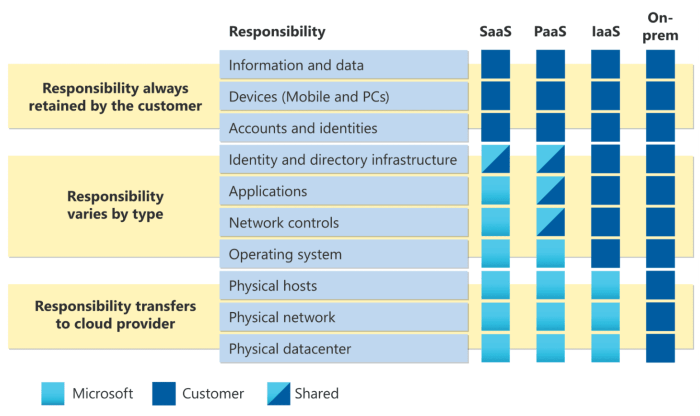
Cloud computing's scalability demands stringent security measures, making clear role and responsibility definitions for cloud access paramount. This a...
This comprehensive article delves into the critical role of tokenization in modern data security, exploring its core concepts, operational mechanisms,...
This article explores the critical need to protect "data in use," delving into the inherent security risks and challenges associated with active compu...
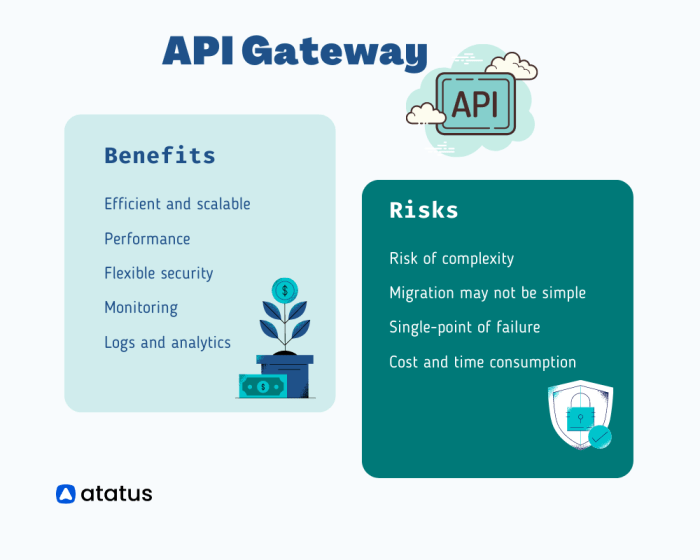
API gateways are vital components of modern application architectures, acting as the primary point of entry and security for all API traffic. Understa...

This comprehensive guide explores Interactive Application Security Testing (IAST), detailing its fundamental principles, advantages, and practical imp...

This article provides a comprehensive guide to preventing SQL injection attacks specifically within cloud application environments. It covers critical...