
Kubernetes Pod Security Policies: Understanding and Implementing Best Practices
Kubernetes Pod Security Policies (PSPs) are crucial for bolstering the security of your containerized applications within a Kubernetes cluster. These...
152 posts in this category

Kubernetes Pod Security Policies (PSPs) are crucial for bolstering the security of your containerized applications within a Kubernetes cluster. These...
In the face of escalating cyber threats, protecting web applications is more critical than ever. This article delves into the essential function of We...
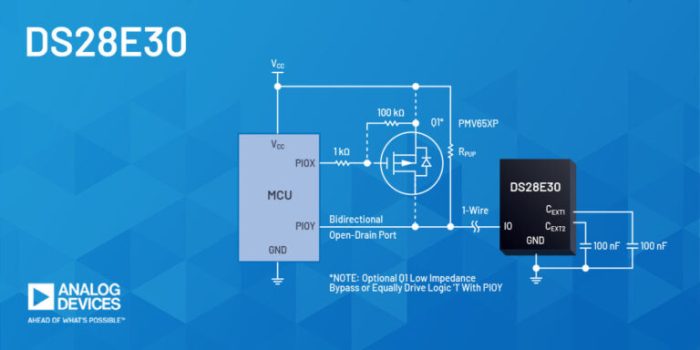
The proliferation of Internet of Things (IoT) devices necessitates robust security measures to protect against increasingly sophisticated cyber threat...
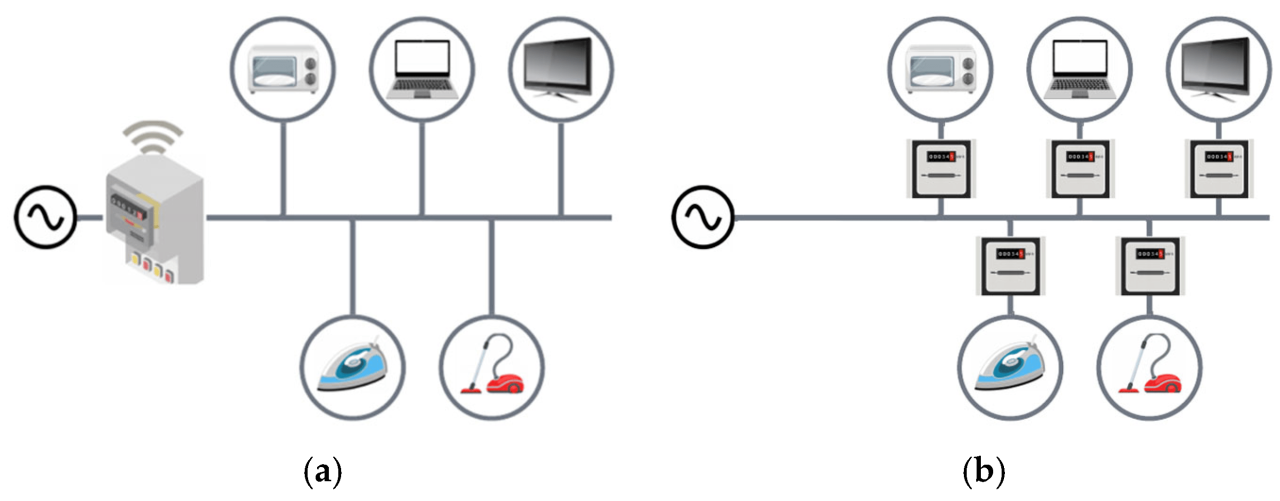
Facing an increasingly complex cyber threat landscape, security operations teams need efficient solutions. This article explores how Security Orchestr...

This article provides a comprehensive overview of the roles and responsibilities within a Security Operations Center (SOC), crucial for modern cyberse...
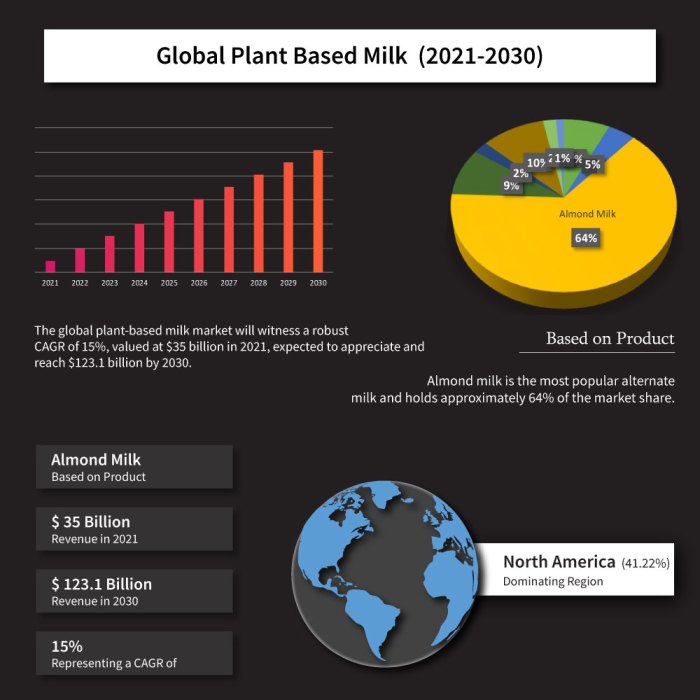
Cybersecurity is a dynamic field, and bolstering your security posture requires a proactive, ongoing approach. This article outlines a strategic frame...

This article provides an introduction to threat modeling using the STRIDE methodology, a critical practice for enhancing software security. Learn how...
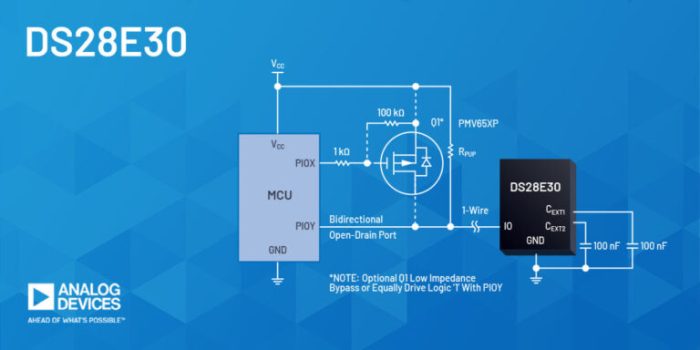
Protecting sensitive data in the cloud requires robust security measures, and this guide provides a comprehensive overview of data encryption. It delv...
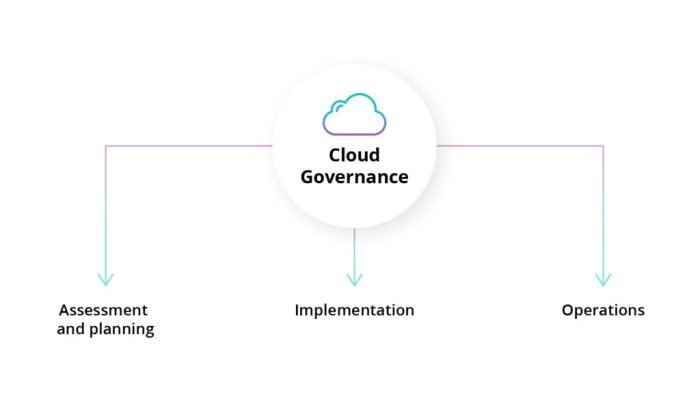
Establishing a formal cloud security governance framework is crucial for protecting valuable assets and maintaining compliance in the cloud. This fram...

This article explores the pivotal role of service meshes in securing modern, microservices-based application architectures. It highlights how service...

This comprehensive guide explores the ISO 27001 standard, a globally recognized framework for information security management. From its core principl...
Protecting sensitive data in the digital age demands robust security measures. This guide provides a detailed overview of enforcing strong authenticat...