
SOC 2 Compliance in the Cloud: A Comprehensive Guide
Navigating SOC 2 compliance in a cloud environment requires a strategic approach, and this article provides a comprehensive guide. It covers essential...
152 posts in this category

Navigating SOC 2 compliance in a cloud environment requires a strategic approach, and this article provides a comprehensive guide. It covers essential...
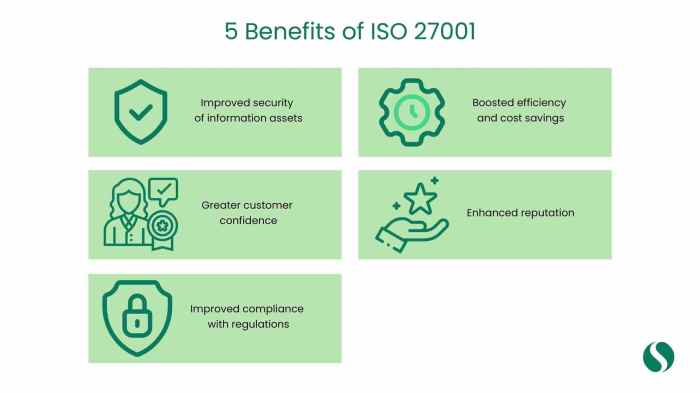
This comprehensive guide provides a detailed roadmap for achieving ISO 27001 certification, covering everything from understanding the core principles...

Discover how Open Policy Agent (OPA) is transforming policy enforcement in modern software development. This guide explores OPA's capabilities in mana...

This article comprehensively explores the "Right to Be Forgotten," a critical aspect of data privacy laws, detailing its origins, legal frameworks, an...
The increasing convergence of Internet of Things (IoT) devices and cloud services necessitates a thorough examination of the associated security risks...
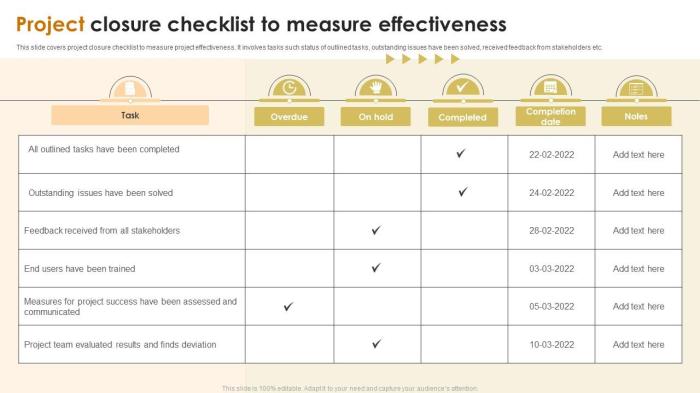
In today's evolving threat landscape, measuring the effectiveness of your security program is paramount. This guide provides a structured approach to...
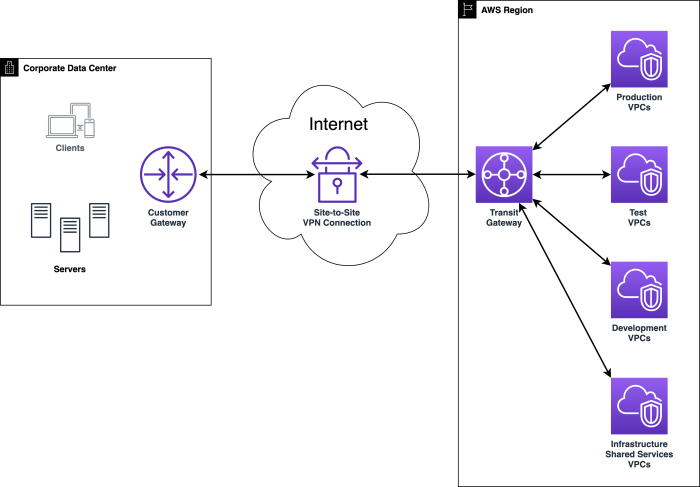
Understand the critical role of Virtual Private Networks (VPNs) in securing modern corporate communications. This article explores the core functional...

The NIST Cybersecurity Framework is a widely adopted, voluntary standard designed to help organizations proactively manage and reduce cybersecurity ri...