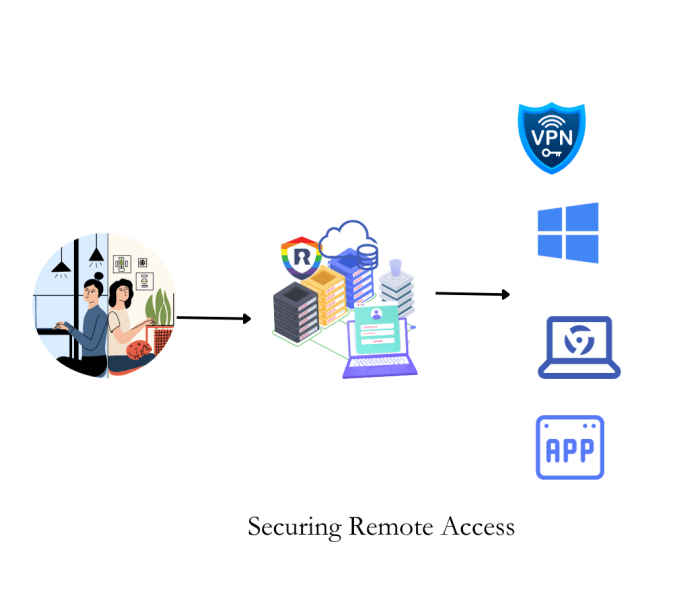
Securing Remote Access to Cloud Environments: Best Practices & Strategies
Securing remote access to cloud environments is paramount in today's interconnected landscape, yet presents significant security challenges. This guid...
152 posts in this category

Securing remote access to cloud environments is paramount in today's interconnected landscape, yet presents significant security challenges. This guid...

This comprehensive guide provides a roadmap for building a robust Security Operations Center (SOC) specifically designed for the cloud environment. Fr...

In the ever-evolving digital world, File Integrity Monitoring (FIM) serves as a crucial security layer, vigilantly protecting your data and systems fr...

This article provides a comprehensive overview of cloud-native security services, exploring their core concepts, key components, and numerous benefits...

In today's dynamic digital landscape, Cloud Security Posture Management (CSPM) is essential for securing your cloud environments. CSPM offers a compre...

This comprehensive article delves into the emerging field of Confidential Computing, defining its core concepts, key technologies, and significant ben...
In today's dynamic digital environment, automating security policy enforcement is paramount. This guide provides a comprehensive overview, covering es...

This comprehensive guide provides a crucial roadmap for securing Infrastructure as Code (IaC) templates, addressing the inherent security challenges o...
This article provides a comprehensive overview of endpoint security specifically tailored for cloud workloads, outlining its core concepts, essential...
User Lifecycle Management (ULM) and provisioning are crucial for security, operational efficiency, and compliance within any organization. This guide...

This article delves into the critical process of de-provisioning user accounts, explaining its definition, triggers, and the vital role it plays in bo...
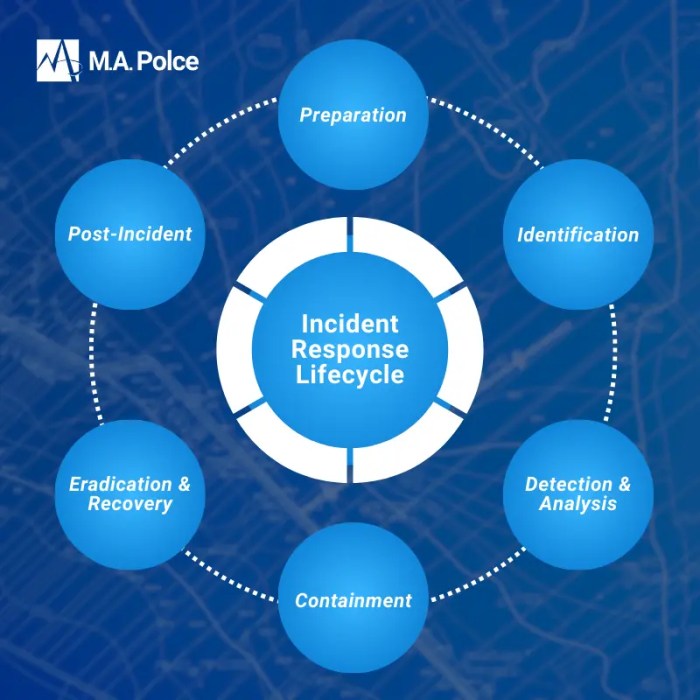
In the face of ever-evolving cyber threats, tabletop exercises are vital for strengthening an organization's incident response capabilities. These dyn...