
Security Challenges in Serverless Computing: A Comprehensive Guide
This article delves into the critical security challenges inherent in serverless computing, covering everything from authentication and authorization...
152 posts in this category

This article delves into the critical security challenges inherent in serverless computing, covering everything from authentication and authorization...

A security baseline serves as the foundation for robust cybersecurity, providing a standardized configuration for systems and applications to ensure a...
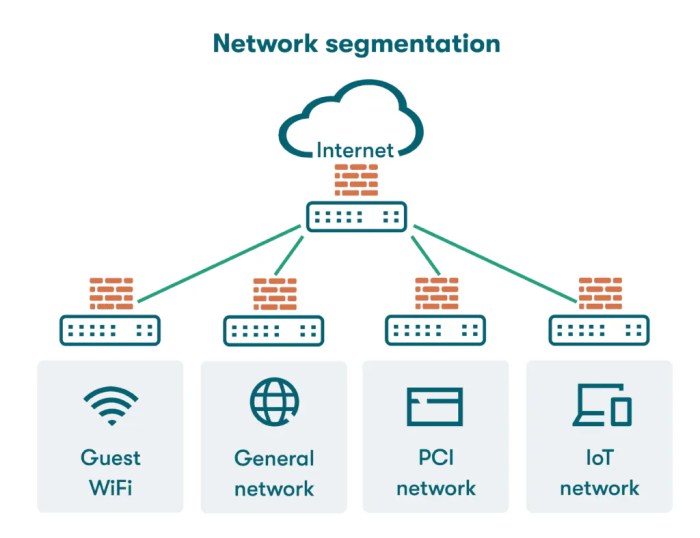
This comprehensive guide provides a deep dive into network segmentation, a crucial strategy for bolstering your organization's security posture. From...

Digital Rights Management (DRM) is a critical component of the digital landscape, serving to protect intellectual property in the realm of content cre...

In the ever-evolving cloud environment, safeguarding your digital assets is critical, and Cloud Infrastructure Entitlement Management (CIEM) tools off...

This comprehensive guide delves into the critical role of Cloud Workload Protection Platforms (CWPP) in modern cloud security, exploring its core conc...

This comprehensive article delves into Runtime Application Self-Protection (RASP), exploring its fundamental concepts, architecture, and operational m...
This comprehensive guide provides a roadmap for understanding and implementing the National Institute of Standards and Technology (NIST) Cybersecurity...

This article provides a comprehensive overview of the Common Vulnerabilities and Exposures (CVE) database, detailing its purpose, structure, and the r...
This article provides a comprehensive guide to implementing CIS Benchmarks for cloud hardening, covering crucial aspects from understanding the benchm...
Securing cloud resources is critical, and implementing Least Privilege Access (LPA) is a foundational security practice. LPA limits user and applicati...

This article provides a comprehensive guide to Tactics, Techniques, and Procedures (TTPs), crucial elements for understanding and combating cyber thre...