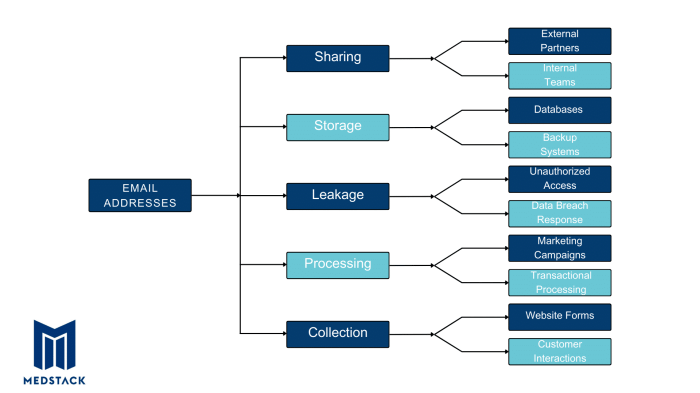
GDPR Data Residency and Sovereignty: Technical Controls for Compliance
This article explores the critical technical controls necessary for organizations to comply with GDPR regulations concerning data residency and sovere...
152 posts in this category

This article explores the critical technical controls necessary for organizations to comply with GDPR regulations concerning data residency and sovere...

Navigate the complex legal landscape of cloud computing with this comprehensive guide. This article delves into critical areas like data privacy regul...

Cloud systems demand constant vigilance to ensure both security and optimal performance. This guide outlines essential strategies and best practices f...

In the digital age, the integrity and admissibility of digital evidence are paramount for successful investigations. This article delves into the cruc...
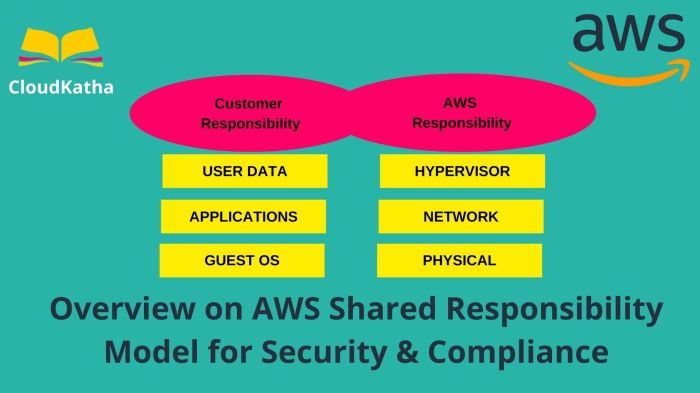
The shared responsibility model is a critical framework in cloud security, outlining the security obligations of both the cloud provider and the custo...
This article provides a comprehensive guide to preventing Cross-Site Scripting (XSS) attacks, detailing the fundamental concepts, various attack types...

This article provides a comprehensive overview of runtime security for containers, emphasizing its critical role in protecting containerized applicati...

In today's digital environment, understanding the financial ramifications of a data breach is essential for any organization. This comprehensive guide...

This comprehensive guide to Cloud Identity and Access Management (IAM) explores core concepts, best practices, and emerging trends to secure your clou...

This guide provides a comprehensive overview of how to launch a successful career in the dynamic field of cloud security. It offers practical advice a...
This comprehensive article explores the concept of honeypots in cybersecurity, detailing their purpose, diverse types (low, medium, and high-interacti...

This article delves into the OWASP Top 10, the definitive guide to web application security risks. It provides a comprehensive overview of the most c...