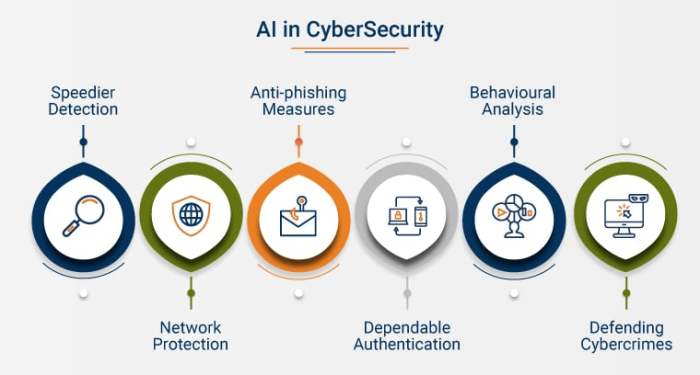
Integrating Threat Intelligence for Enhanced Cloud Security Operations
This article explores the vital integration of threat intelligence into cloud security operations, a crucial step in defending against modern cyber th...
152 posts in this category

This article explores the vital integration of threat intelligence into cloud security operations, a crucial step in defending against modern cyber th...

This article delves into the intricacies of identity federation, explaining its core concepts, components, and the benefits it offers for streamlined...

This article delves into the critical practice of Continuous Compliance Monitoring (CCM) in cloud environments, explaining its core concepts and showc...

Organizations face increasing cyber threats, making robust security awareness training for employees crucial. This comprehensive guide provides a step...

This article provides a comprehensive overview of security maturity models, essential frameworks for enhancing an organization's cybersecurity posture...

Discover insights and practical tips in this comprehensive guide about What Are The Compliance Requirements For Data Breach Notifications.

Cloud governance is essential for successful cloud adoption, and "policy as code" is revolutionizing how organizations manage and secure their environ...
Navigating a cloud security audit can seem daunting, but this comprehensive guide provides a clear roadmap for preparation and success. The article me...
In today's cloud-centric world, understanding Data Loss Prevention (DLP) solutions is critical for safeguarding sensitive information. This article pr...
In an era defined by digital interconnectedness, cyber insurance has become a critical safeguard for businesses facing persistent online threats. This...

Cloud environments present unique challenges for security forensics, but understanding the core principles is crucial for effective investigation. Thi...
Managing security across a multi-cloud environment requires a strategic approach to avoid fragmentation and ensure consistent protection. This guide o...