AI's Transformation of Cybersecurity: Challenges and Opportunities
Artificial intelligence is rapidly transforming the cybersecurity landscape, offering powerful new tools for threat detection, incident response, and...
152 posts in this category

Artificial intelligence is rapidly transforming the cybersecurity landscape, offering powerful new tools for threat detection, incident response, and...
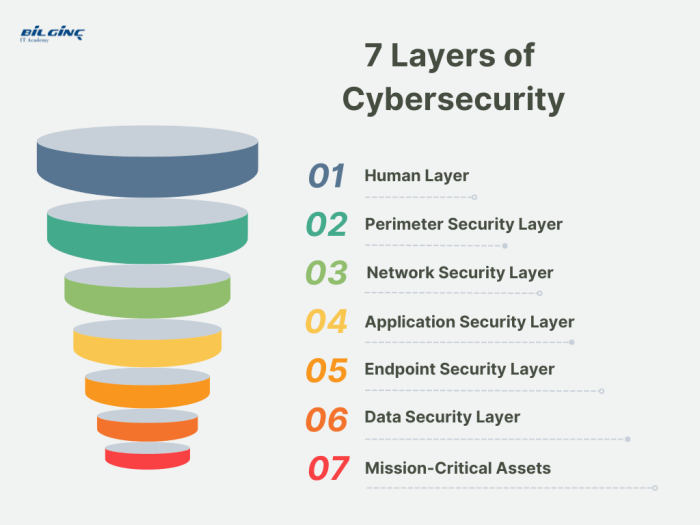
Defense in depth is a critical cybersecurity principle that emphasizes a layered approach to security, acknowledging that no single measure is impenet...
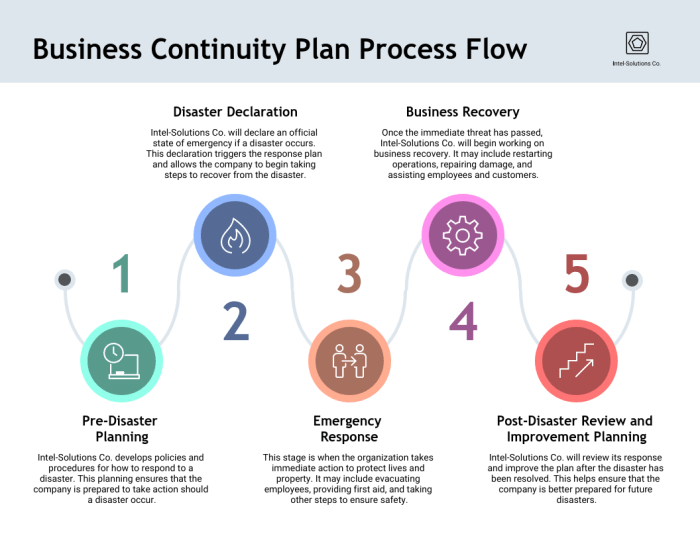
This comprehensive guide explores the essential integration of Business Continuity Planning (BCP) and Disaster Recovery (DR), providing a roadmap to e...
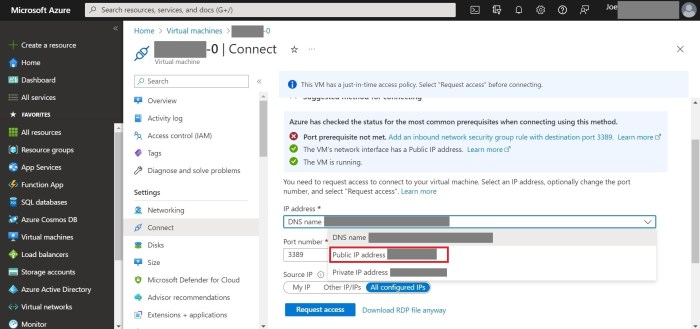
This article delves into the critical concept of Just-in-Time (JIT) access for cloud resources, exploring its core principles and the significant secu...

Navigating the complexities of cloud security requires a proactive approach, beginning with a comprehensive incident response plan. This guide highlig...

This article provides a comprehensive analysis of proactive versus reactive security strategies, detailing their core principles, advantages, and limi...
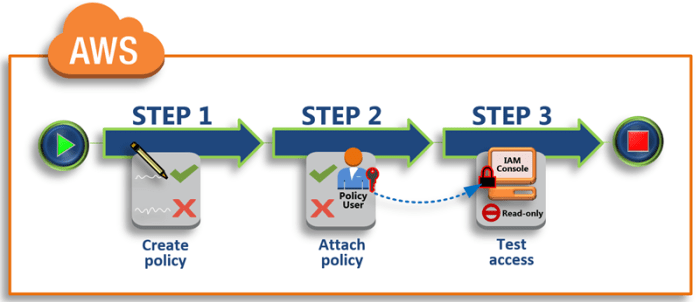
This comprehensive guide delves into the world of Identity and Access Management (IAM) policies, explaining their crucial role in securing access to y...

This comprehensive guide explores the critical importance of securing your software dependencies, outlining potential risks from supply chain attacks...
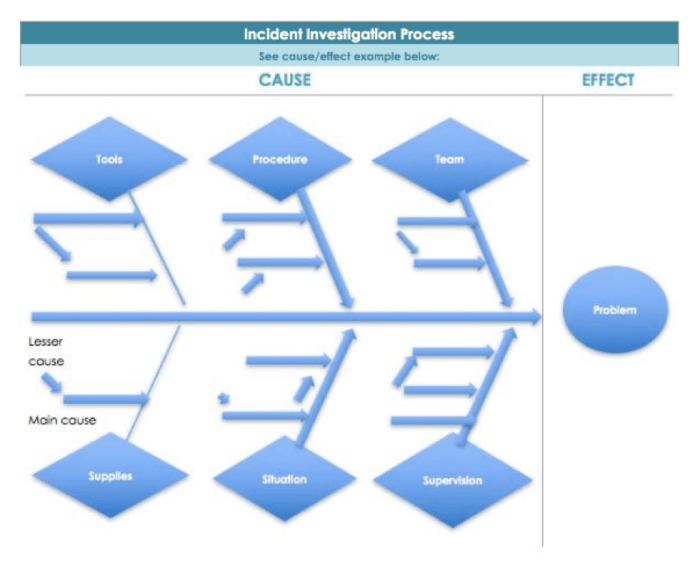
This article provides a comprehensive guide to performing a Root Cause Analysis (RCA) following a security incident, a crucial skill in today's digita...
This comprehensive guide outlines the crucial steps for conducting regular cloud security risk assessments, ensuring the protection of your valuable a...

This article provides a comprehensive overview of Cloud Access Security Brokers (CASBs), outlining their core functions, architecture, and key feature...
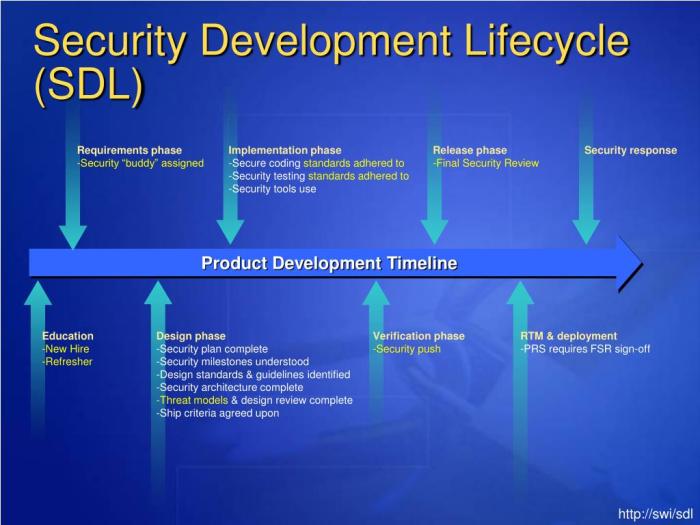
"Shifting security left" is a critical strategy for modern software development, emphasizing the integration of security practices early in the develo...