Automate Database Schema Migrations: A Practical Guide
This article delves into the critical process of automating database schema migrations, exploring the benefits of automation and the challenges of man...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

This article delves into the critical process of automating database schema migrations, exploring the benefits of automation and the challenges of man...
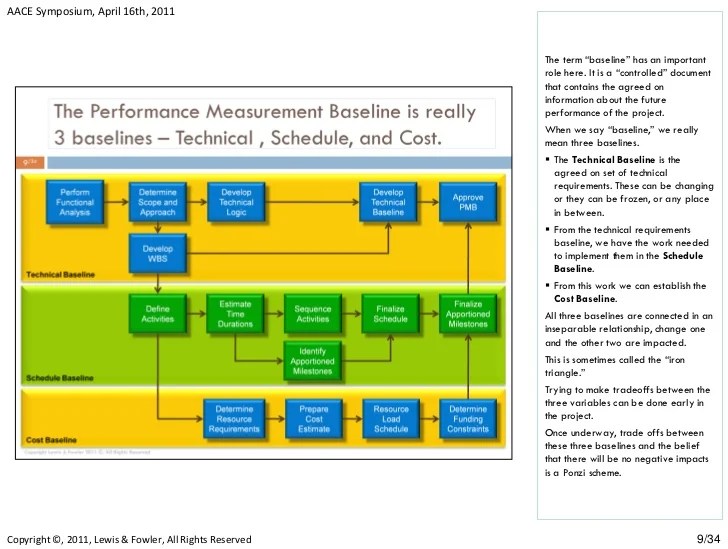
Baseline performance benchmarking is a critical process for understanding and enhancing system or process efficiency. By establishing a clear baseline...
This article delves into the vital practice of explicitly declaring and isolating dependencies, a key component of robust and scalable software develo...

Organizations face increasing cyber threats, making robust security awareness training for employees crucial. This comprehensive guide provides a step...

This article provides a comprehensive overview of Amazon Aurora Serverless, exploring its core concepts, architecture, and benefits for database manag...
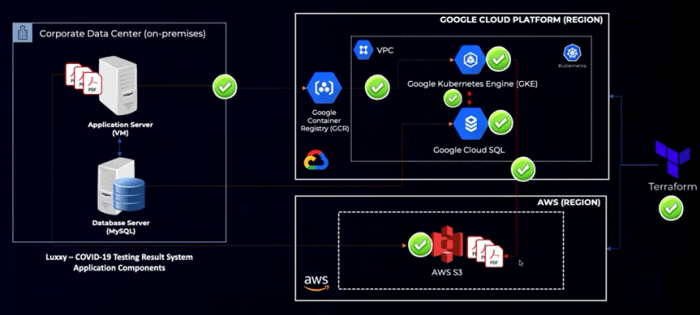
Navigating the multi-cloud landscape presents significant challenges, ranging from increased complexity and security concerns to cost management and s...

Cloud cost forecasting is crucial for businesses leveraging the cloud's benefits, as fluctuating expenses can be a major hurdle. This article delves i...
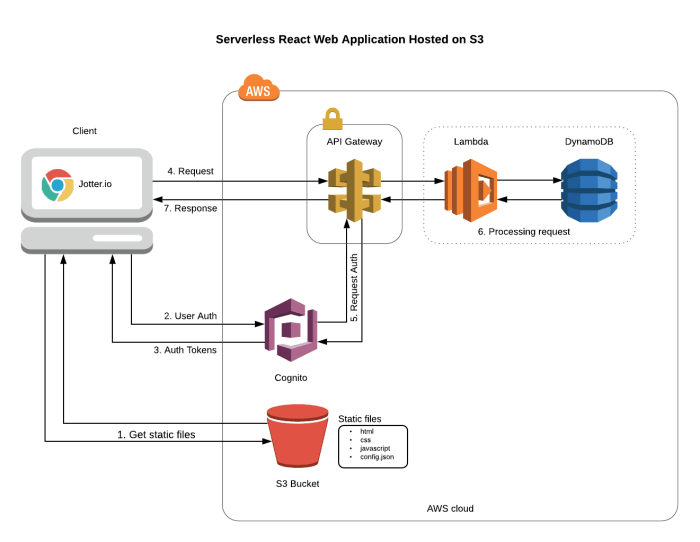
Serverless architecture is revolutionizing web application development by simplifying backend management and optimizing resource utilization. This par...

Managing microservices communication presents intricate challenges, but Istio offers a comprehensive solution. This guide explores Istio's capabilitie...
Migrating your Enterprise Resource Planning (ERP) system to the cloud is a transformative step that can significantly enhance efficiency, scalability,...

Successfully migrating a system is only the initial phase; long-term operational tasks are crucial for sustained success. This article delves into th...
This article provides a thorough exploration of phishing attacks, outlining their deceptive tactics and potential impact on your digital security. Lea...