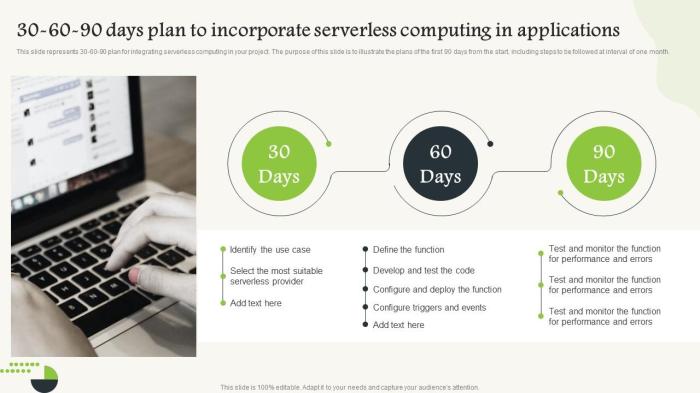
Serverless Execution Time Limits: Understanding and Optimizing Your Function's Runtime
Serverless computing revolutionizes application development by abstracting away infrastructure management, but it introduces execution time limits tha...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

Serverless computing revolutionizes application development by abstracting away infrastructure management, but it introduces execution time limits tha...
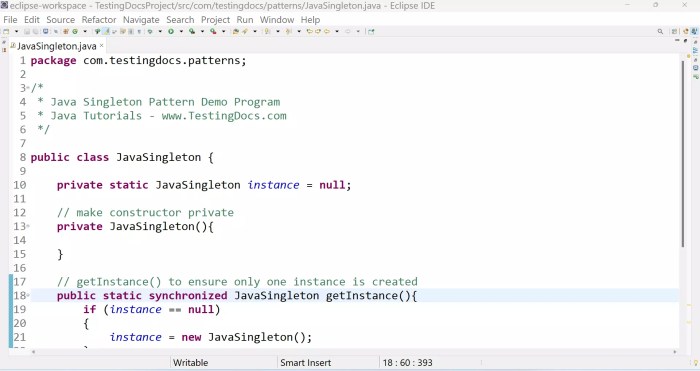
The Singleton pattern provides a method for controlling object instantiation, ensuring only one instance of a class exists with global access. While t...
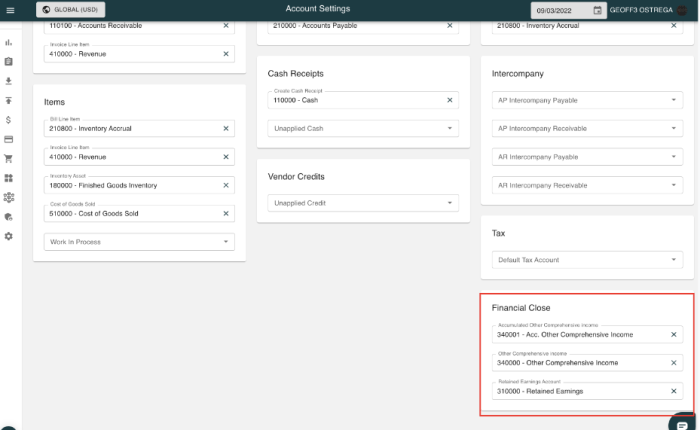
Configuration drift in security settings poses a significant threat, potentially weakening your defenses through unnoticed changes. Proactively monito...
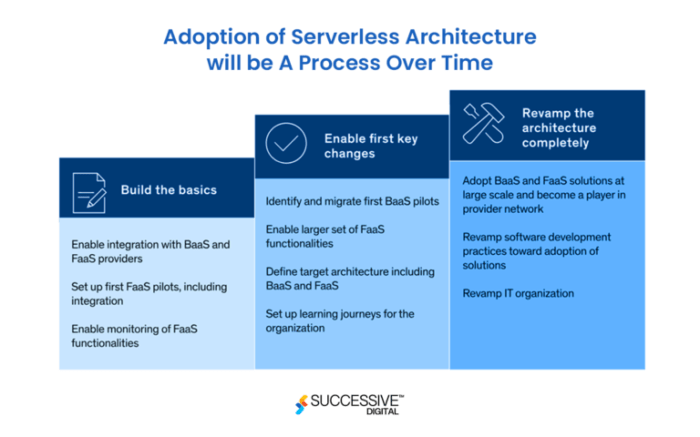
This article delves into the essential role of CloudEvents in the modern serverless landscape, exploring how this standard promotes interoperability a...

Green cloud computing is transforming the technology landscape by prioritizing environmental sustainability within cloud infrastructure. This approach...

This guide provides a comprehensive approach to crafting effective postmortem documents, crucial for analyzing incidents and fostering continuous impr...

This comprehensive guide delves into the world of distributed tracing, providing a detailed roadmap for implementing this crucial practice within micr...
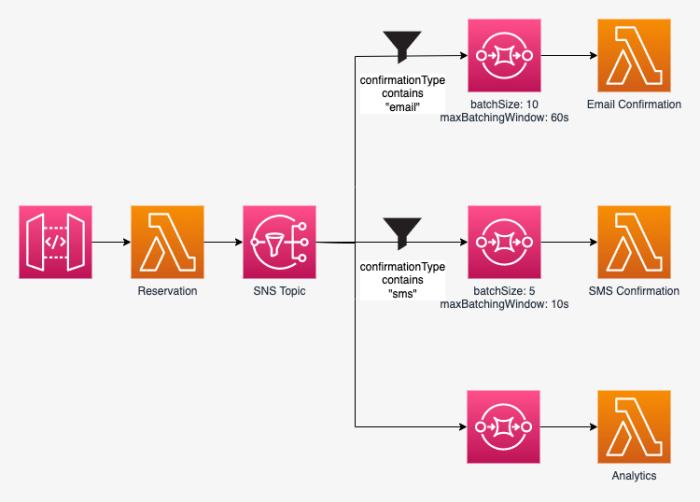
This article provides a comprehensive guide to leveraging Amazon SNS for efficient message fan-out to AWS Lambda functions. Readers will learn how to...

Infrastructure as Code (IaC) has transformed cloud computing, offering automation and version control for efficient infrastructure management. This ar...

Protecting sensitive data within big data platforms demands a comprehensive approach encompassing encryption, access control, data governance, and rob...

Data classification is a fundamental practice in information security, involving the categorization of data based on its sensitivity and importance. T...

Protecting sensitive data within Kubernetes is crucial for the security of your deployments. This article provides a comprehensive guide to managing s...