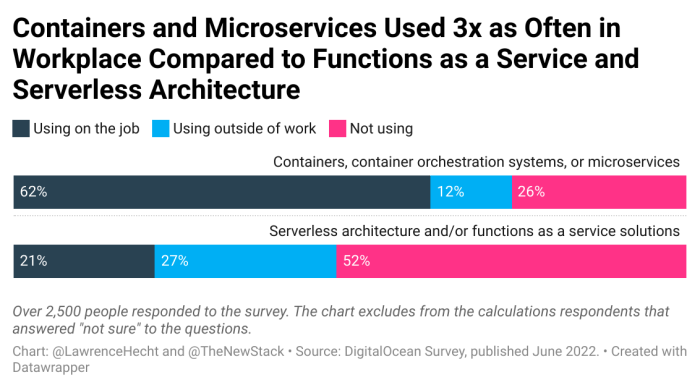
Serverless Interview Questions: Prepare for Your Next Cloud Role
This comprehensive guide delves into the world of serverless computing, equipping you with the knowledge to ace your next interview. From the fundamen...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

This comprehensive guide delves into the world of serverless computing, equipping you with the knowledge to ace your next interview. From the fundamen...

Facing database schema changes? This guide provides essential strategies for implementing them without disrupting your application's availability. Lea...

This article comprehensively explores the "Right to Be Forgotten," a critical aspect of data privacy laws, detailing its origins, legal frameworks, an...
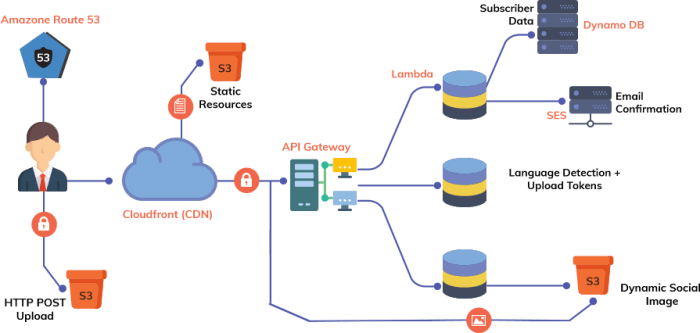
This article delves into the critical aspects of optimizing the inner loop development process for serverless applications, addressing common bottlene...

Cloud-based businesses are increasingly vulnerable to Distributed Denial of Service (DDoS) attacks, which can disrupt online services and lead to subs...

Cloud governance is essential for successful cloud adoption, and "policy as code" is revolutionizing how organizations manage and secure their environ...
System migrations can disrupt user workflows, making a comprehensive support strategy crucial for a smooth transition. This article explores essential...

Migrating databases to the cloud presents a complex set of challenges, ranging from data format conversions and ensuring data integrity to navigating...
This guide offers a comprehensive walkthrough of creating a Helm chart for your application, a key practice for modern Kubernetes deployments. Learn t...

This comprehensive guide explores the ISO 27001 standard, a globally recognized framework for information security management. From its core principl...

This article provides a comprehensive overview of security maturity models, essential frameworks for enhancing an organization's cybersecurity posture...
Large-scale message processing systems rely on effective strategies for handling high volumes and ensuring reliable delivery. The "Claim Check Patter...