
HIPAA Compliance: Key Architectural Considerations for Healthcare Systems
This comprehensive guide explores the critical architectural considerations for achieving HIPAA compliance, covering essential areas such as data secu...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

This comprehensive guide explores the critical architectural considerations for achieving HIPAA compliance, covering essential areas such as data secu...

Safeguarding your cloud environment begins with a thorough vulnerability assessment. This guide provides a structured approach to identifying and miti...
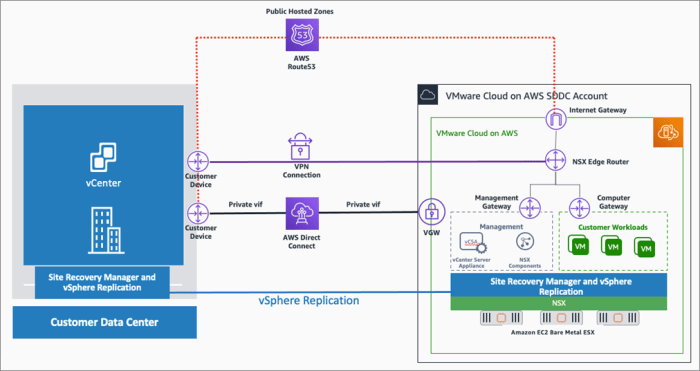
Ensuring business continuity in the cloud necessitates robust disaster recovery testing. This article explores the critical process of evaluating clou...
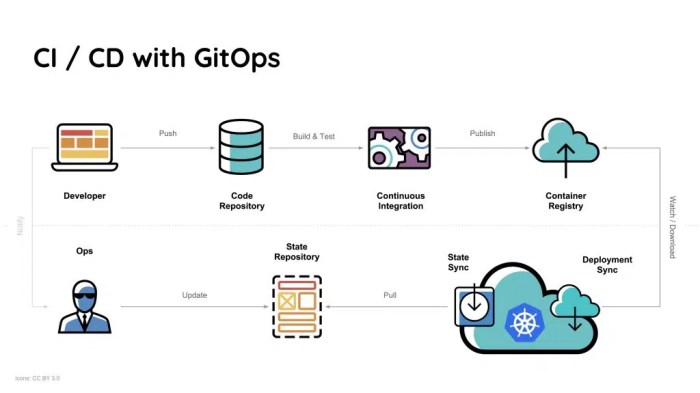
GitOps is a modern approach to infrastructure and application management, utilizing Git as the central source of truth for streamlined deployments and...

Observability is essential for modern system management, providing the tools to understand and optimize application performance. This article explores...
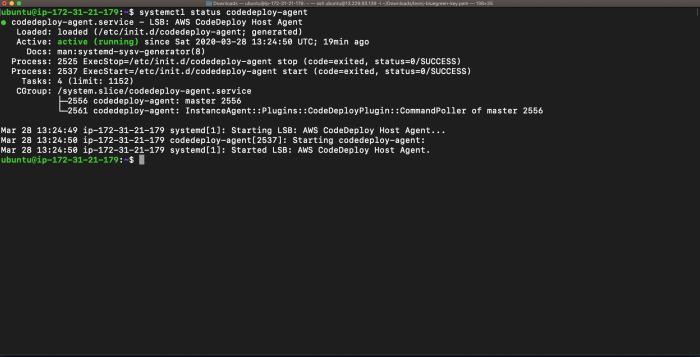
This article delves into the practical implementation of blue-green deployments for AWS Lambda functions, a critical strategy for achieving continuous...
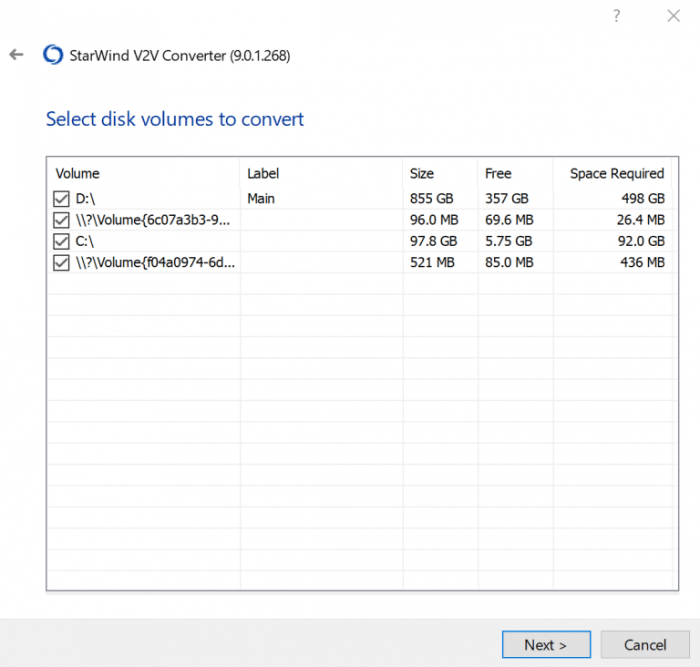
This comprehensive article explores Physical to Virtual (P2V) migration, a crucial process for modernizing IT infrastructure. From fundamental concept...
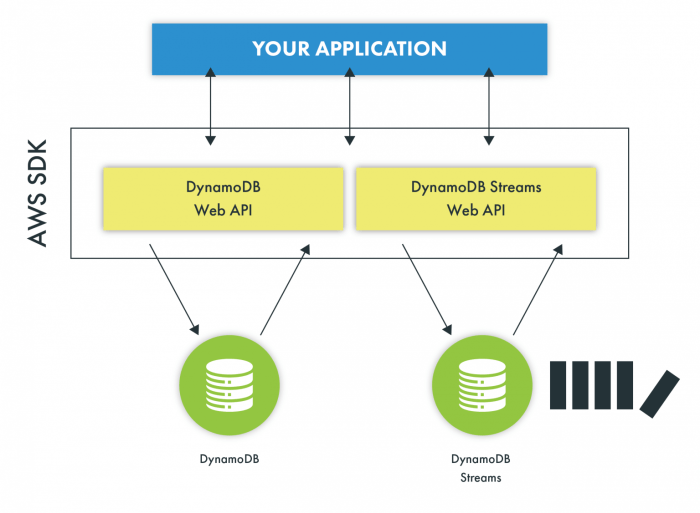
This article provides a comprehensive guide to understanding and implementing effective DynamoDB access patterns. It delves into common patterns like...

This comprehensive guide provides a roadmap for assessing and elevating your organization's FinOps maturity, offering a deep dive into the core princi...

Cloud computing's benefits hinge on the reliability of its underlying systems. This guide provides a comprehensive overview of designing robust cloud...
This comprehensive article delves into the transformative technology of homomorphic encryption, exploring its core functionality, diverse types, and u...
Debugging containerized applications requires a specialized approach, distinct from traditional methods. This article provides a comprehensive guide,...