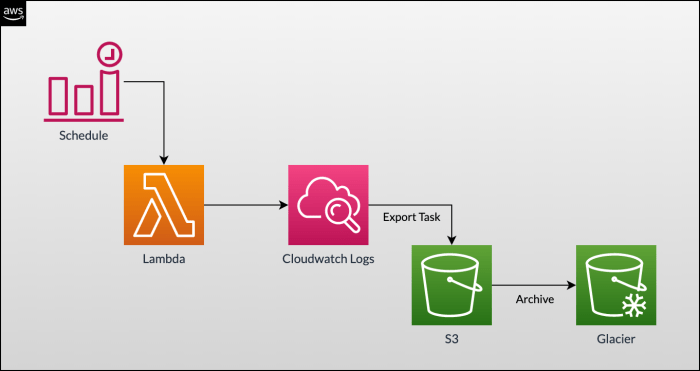
Monitoring Lambda Functions: A Guide to Using CloudWatch Logs
Effectively monitoring and troubleshooting your serverless applications hinges on understanding CloudWatch Logs for Lambda functions. This central rep...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

Effectively monitoring and troubleshooting your serverless applications hinges on understanding CloudWatch Logs for Lambda functions. This central rep...

Migration projects often face resistance to change, stemming from psychological factors and concerns about the unknown. To ensure a successful transit...

This article delves into the critical security challenges inherent in serverless computing, covering everything from authentication and authorization...

Explore the robust Hexagonal Architecture pattern in this comprehensive guide, covering its core principles, benefits, and practical implementation. T...

Embarking on a cloud migration journey? This comprehensive guide provides a detailed checklist for enterprises, outlining the critical steps from init...
Successfully integrating cloud architecture with business objectives is paramount for maximizing value and achieving strategic goals. This guide offer...
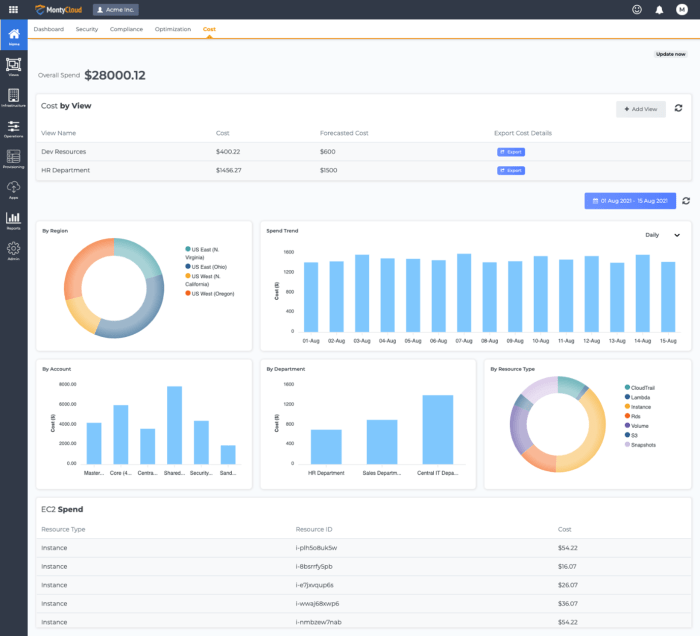
Managing cloud costs effectively is a significant hurdle for organizations, often leading to unexpected expenses and inefficient resource allocation....

MLOps represents a vital shift in how organizations approach machine learning, integrating it seamlessly with IT operations. This methodology streamli...
Serverless computing is undergoing a crucial transformation as it adapts to handle stateful workloads, a departure from its historical focus on statel...
This article delves into the critical role of Continuous Integration (CI) within modern DevOps, highlighting its evolution from a nascent practice to...
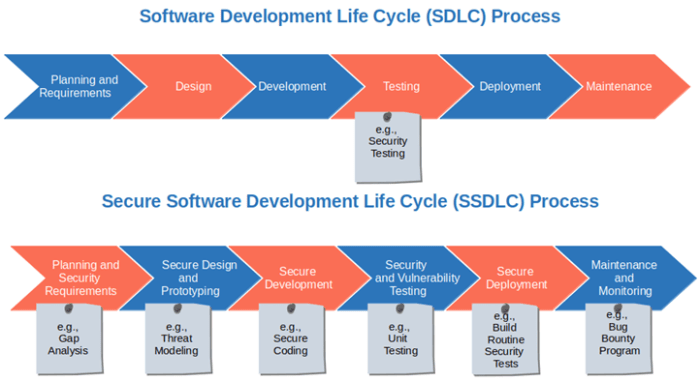
Protecting your software from vulnerabilities is paramount in today's digital world, and this guide provides a comprehensive approach to implementing...

In today's data-driven world, protecting sensitive information is critical, and Key Management Services (KMS) are essential for achieving this. This a...