
Threat Modeling with STRIDE: A Step-by-Step Guide
This article provides an introduction to threat modeling using the STRIDE methodology, a critical practice for enhancing software security. Learn how...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

This article provides an introduction to threat modeling using the STRIDE methodology, a critical practice for enhancing software security. Learn how...

This article delves into the critical process of de-provisioning user accounts, explaining its definition, triggers, and the vital role it plays in bo...

Effectively managing cloud spending is critical for businesses in today's digital environment. This article outlines the essential strategies for trac...
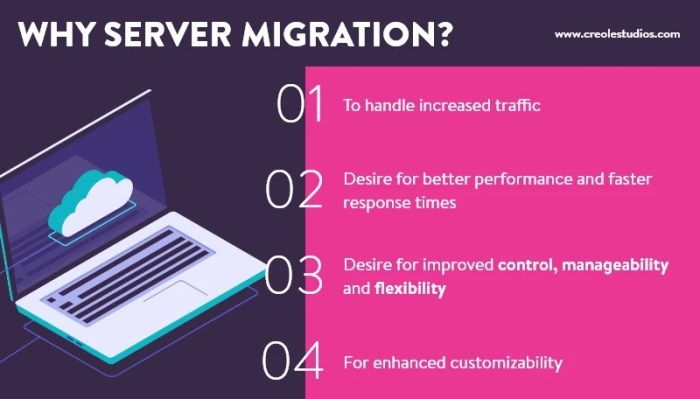
Migrating your DNS can be a complex process, but this article provides a comprehensive guide to ensure a smooth and successful cutover. It covers cruc...

This comprehensive guide outlines a strategic approach to conducting a quarterly cloud cost review, enabling organizations to gain control over their...

Building an effective DevOps toolchain requires careful consideration of your team's needs, budget, and long-term goals. This comprehensive guide expl...
Maximize your serverless computing efficiency by understanding the AWS Lambda Free Tier. This article provides a comprehensive overview of the free ti...

Discover insights and practical tips in this comprehensive guide about What Is The Total Cost Of Ownership (Tco) For Cloud.

Edge computing is transforming data processing by minimizing latency and improving response times for real-time applications. By shifting computation...
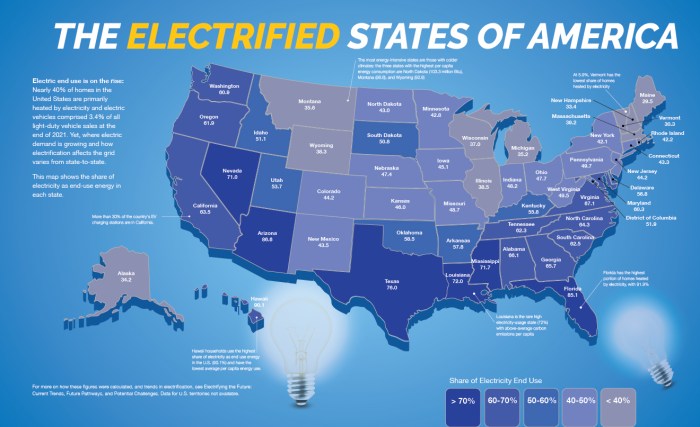
Protecting your business from unforeseen disasters requires a robust recovery plan. This article clarifies the distinctions between cold sites and hot...
Cybersecurity is a dynamic field, and bolstering your security posture requires a proactive, ongoing approach. This article outlines a strategic frame...
In an era defined by digital interconnectedness, cyber insurance has become a critical safeguard for businesses facing persistent online threats. This...