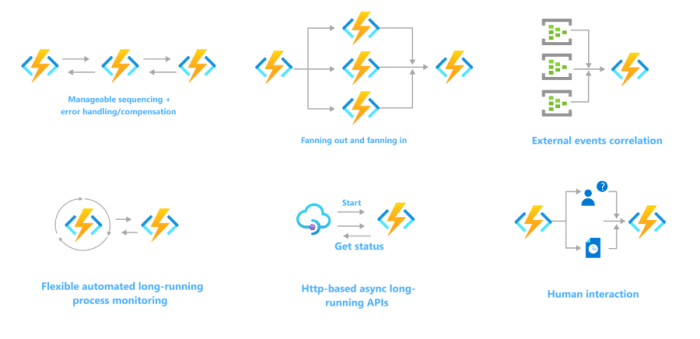
API Composition in Serverless: A Key to Scalable Architectures
This article delves into the critical role of API composition within serverless architectures, exploring how to effectively build, manage, and optimiz...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

This article delves into the critical role of API composition within serverless architectures, exploring how to effectively build, manage, and optimiz...
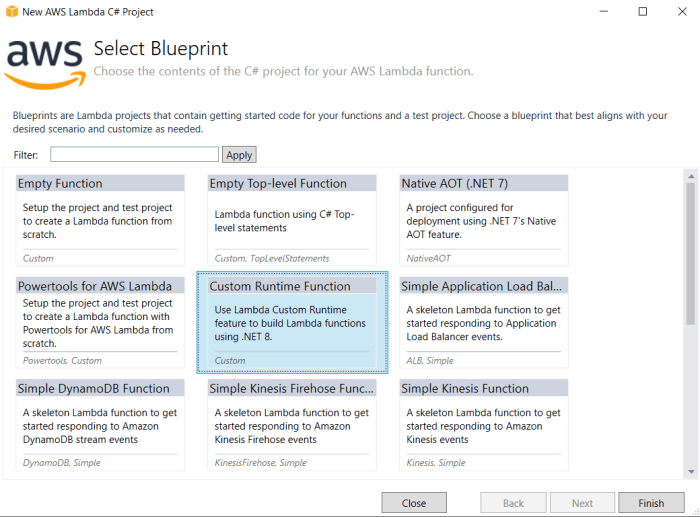
Unlock the full potential of AWS Lambda with custom runtimes. This comprehensive guide delves into the definition, benefits, and implementation of cus...
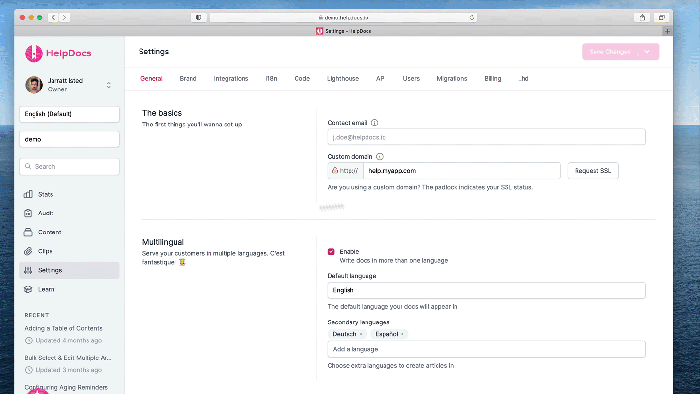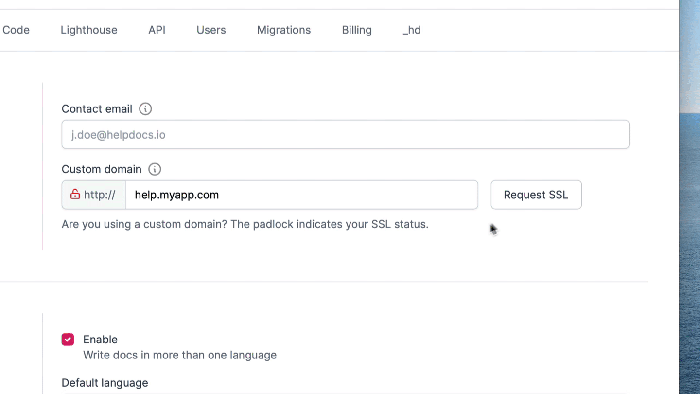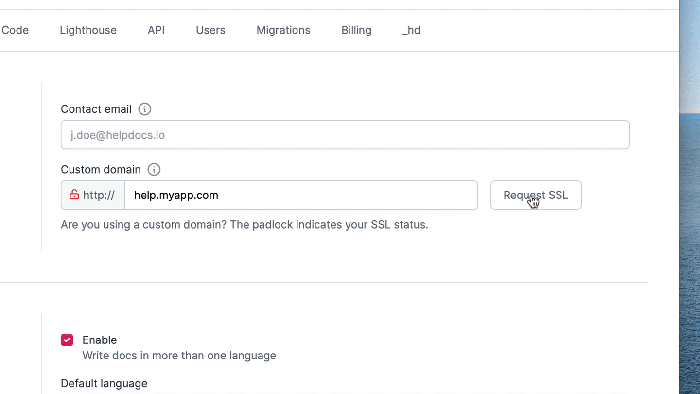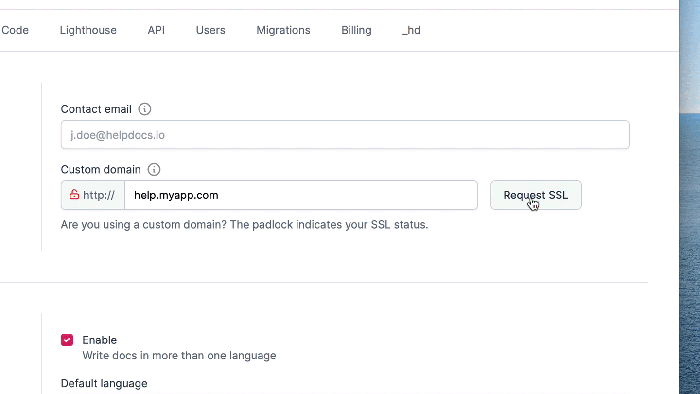
Custom domains are essential for professionalizing your serverless APIs, offering branding, a better user experience, and improved security compared t...

The KISS (Keep It Simple, Stupid) principle is a powerful concept advocating for clarity and efficiency by prioritizing ease of understanding and exec...

This comprehensive guide provides a thorough introduction to Ansible, a powerful tool for automating configuration management. From setting up your en...

Database migration, while essential for data infrastructure upgrades, inherently risks operational downtime. This article explores crucial strategies...
Protecting sensitive information is paramount in today's data-driven world, and this comprehensive guide provides a deep dive into implementing effect...
Containerization and Kubernetes offer a significant advancement in application deployment, driven by the need for improved efficiency and flexibility....

The digital world is constantly evolving, and staying informed about the latest security threats and vulnerabilities is crucial for both individuals a...
Facing escalating cloud costs? This guide provides a crucial roadmap for implementing an IT chargeback model, transforming cloud expenses from a black...
This article provides a comprehensive overview of Chaos Engineering within a DevOps context, detailing its principles, goals, and practical implementa...

This article provides a comprehensive analysis of proactive versus reactive security strategies, detailing their core principles, advantages, and limi...