
Multi-Cloud Security Risks: A Comprehensive Guide
Organizations leveraging multi-cloud environments face a complex landscape of security risks, including data breaches, identity and access management...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

Organizations leveraging multi-cloud environments face a complex landscape of security risks, including data breaches, identity and access management...
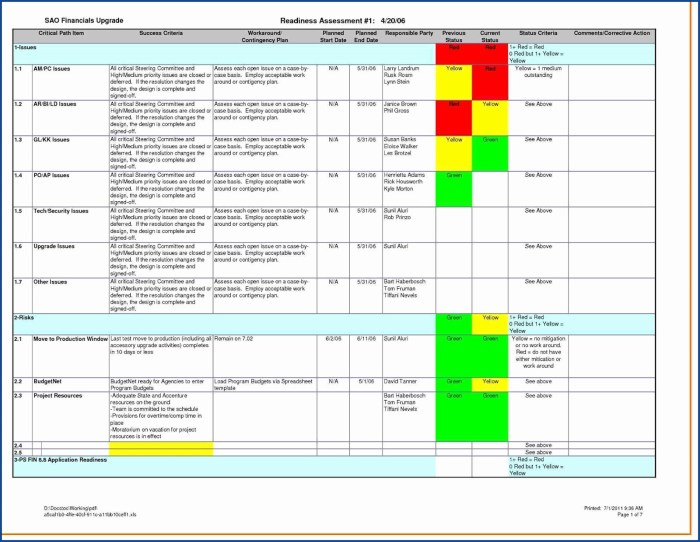
Migrating applications demands a robust approach, and User Acceptance Testing (UAT) is a crucial step in ensuring a successful transition. UAT validat...

Discover insights and practical tips in this comprehensive guide about What Is The Serverless Application Model (Sam).
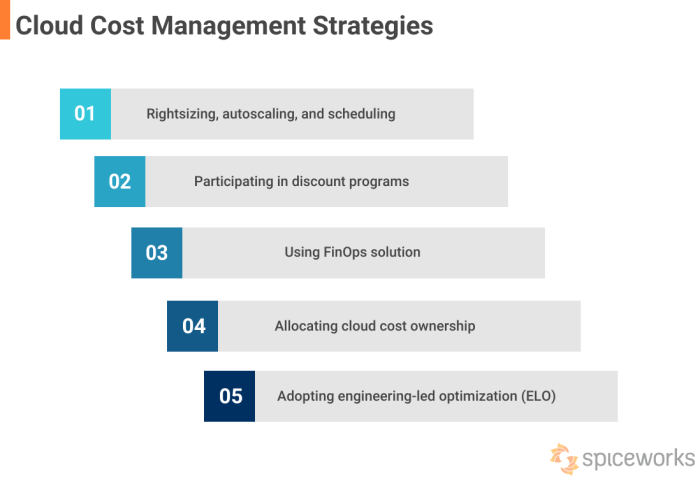
Understanding unit economics is crucial for effective cloud cost management, allowing businesses to optimize spending and maximize return on investmen...
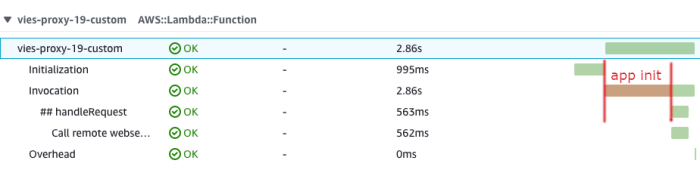
Serverless cold starts can significantly impact application performance, but this comprehensive guide provides actionable strategies to mitigate laten...

This article provides a comprehensive overview of Data Privacy Impact Assessments (DPIAs), essential tools for protecting personal information in the...

This comprehensive guide delves into the intricacies of designing a robust multi-tenant cloud architecture, exploring key benefits, service models, an...

Managing cloud costs effectively is crucial for optimizing cloud investments. This guide, "How to Create a FinOps Playbook for Your Organization," pro...
Integrating FinOps with your financial systems is essential for maximizing cloud spending efficiency and strategic decision-making. This alignment all...
This comprehensive guide explores the implementation of Durable Functions in Azure, providing a deep dive into their core concepts, orchestration patt...

In today's evolving work environment, developing a skilled and prepared team is critical for organizational success. This guide provides a strategic r...
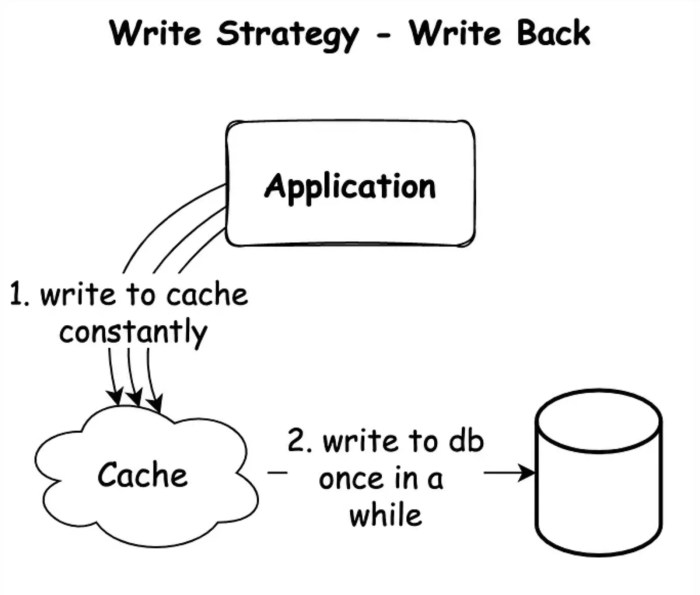
This article delves into the critical distinctions between write-through and write-back caching, two fundamental strategies for optimizing data access...