Embarking on the journey of cloud security requires a steadfast commitment to safeguarding your digital assets. Steps for conducting regular cloud security risk assessments are paramount in this endeavor, providing a proactive approach to identifying and mitigating potential threats. This guide serves as a comprehensive roadmap, detailing the essential stages involved in securing your cloud environment and ensuring its resilience against evolving cyber threats.
From defining the scope of your assessment to implementing and validating security controls, this Artikel meticulously covers each phase of the process. We delve into crucial aspects such as asset identification, threat modeling, risk analysis, and continuous monitoring, equipping you with the knowledge and tools necessary to establish a robust cloud security posture. By understanding the unique considerations of major cloud providers and adopting best practices, you can confidently navigate the complexities of cloud security and protect your valuable data.
Defining the Scope of Cloud Security Risk Assessments
Defining the scope of a cloud security risk assessment is the foundational step. A well-defined scope ensures that the assessment is focused, efficient, and provides meaningful results. It sets the boundaries of the assessment, clarifying what will be examined and what will be excluded. Without a clear scope, the assessment can become unfocused, leading to wasted resources, incomplete analysis, and ultimately, ineffective security improvements.
Cloud Environment Components
Identifying and documenting all components within the cloud environment is critical for a comprehensive assessment. This includes all infrastructure-as-a-service (IaaS), platform-as-a-service (PaaS), and software-as-a-service (SaaS) offerings utilized. A detailed inventory allows for targeted analysis of potential vulnerabilities and risks associated with each component.
- Compute Resources: This includes virtual machines (VMs), containers (e.g., Docker, Kubernetes), and serverless functions (e.g., AWS Lambda, Azure Functions, Google Cloud Functions). Documenting these resources includes their configurations, operating systems, and associated security settings.
- Storage Services: Identify and document all storage solutions used, such as object storage (e.g., Amazon S3, Azure Blob Storage, Google Cloud Storage), block storage, and file storage. This should include access controls, encryption methods, and data retention policies.
- Networking Components: This encompasses virtual networks, subnets, firewalls, load balancers, and VPN connections. Mapping the network architecture helps understand the flow of traffic and potential points of compromise.
- Databases: Detail the database services used, including database types (e.g., relational, NoSQL), configurations, and security measures (e.g., encryption, access control lists).
- Applications: List all applications running in the cloud environment, including their purpose, dependencies, and security configurations.
- Identity and Access Management (IAM): Document the IAM systems in use, including users, roles, permissions, and multi-factor authentication (MFA) configurations. This is a critical area as compromised credentials are a common attack vector.
Data Types
Understanding the types of data stored, processed, and transmitted within the cloud environment is crucial for assessing risks. Different data types have varying levels of sensitivity and require different security controls. Failing to account for all data types can lead to inadequate protection and potential data breaches.
- Personally Identifiable Information (PII): This includes data that can be used to identify an individual, such as names, addresses, social security numbers, and financial information. PII requires the highest level of protection due to compliance regulations like GDPR and CCPA.
- Protected Health Information (PHI): This pertains to medical records and health information. PHI is subject to regulations like HIPAA in the United States.
- Financial Data: This includes credit card information, bank account details, and other financial records. Financial data is regulated by standards like PCI DSS.
- Intellectual Property (IP): This covers confidential business information, trade secrets, and proprietary data. IP requires protection from unauthorized access and disclosure.
- Operational Data: This encompasses system logs, configuration files, and other data used for monitoring and managing the cloud environment.
Business Processes
Mapping business processes that utilize cloud services is essential for understanding how the cloud environment supports the organization’s operations. This understanding enables a more focused risk assessment, identifying potential vulnerabilities within critical business functions.
- Application Development and Deployment: Assessing the security of the development pipeline, including code repositories, build processes, and deployment strategies.
- Data Processing and Analytics: Evaluating the security of data pipelines, including data ingestion, storage, processing, and reporting.
- Customer Relationship Management (CRM): Assessing the security of CRM systems, including data access controls, data encryption, and data backup procedures.
- Financial Transactions: Evaluating the security of systems that handle financial transactions, including payment processing and accounting systems.
- Incident Response: Examining the incident response plan and procedures, including how incidents are detected, reported, and resolved.
Documenting the Scope
Documenting the scope of the cloud security risk assessment is best achieved through a checklist or template. This provides a structured approach to ensure all relevant components, data types, and business processes are considered. A well-designed document acts as a reference point throughout the assessment.
Example Checklist/Template Snippet:
| Category | Component/Data Type/Process | Description | In Scope? (Yes/No) | Notes |
|---|---|---|---|---|
| Compute | Virtual Machines (VMs) | All VMs running in AWS EC2 in the us-east-1 region. | Yes | Include all OS types and configurations. |
| Storage | Amazon S3 Buckets | All S3 buckets used for storing customer data. | Yes | Examine access controls and encryption settings. |
| Data Type | Customer PII | Customer names, addresses, and email addresses. | Yes | Assess data encryption and access control measures. |
| Business Process | Order Processing | The process of receiving, processing, and fulfilling customer orders. | Yes | Include payment processing and order fulfillment systems. |
Implications of a Poorly Defined Scope
A poorly defined scope significantly diminishes the effectiveness of a cloud security risk assessment. It can lead to several negative consequences, including:
- Incomplete Assessment: Critical components, data types, or business processes may be overlooked, leaving significant vulnerabilities unaddressed.
- Inefficient Use of Resources: The assessment team may spend time and effort examining areas that are not relevant to the organization’s risk profile, leading to wasted resources.
- Inaccurate Risk Prioritization: Without a clear understanding of the scope, it becomes difficult to accurately prioritize risks, potentially focusing on less critical areas.
- Increased Risk of Data Breaches: By missing key areas, the assessment fails to identify and mitigate vulnerabilities that could lead to a data breach.
- Non-Compliance: Failing to assess all relevant areas may result in non-compliance with regulatory requirements and industry best practices.
Identifying Assets and Data in the Cloud
Understanding and cataloging your cloud assets and data is fundamental to effective cloud security risk assessment. This involves a thorough inventory of all resources and a clear understanding of the data they handle. Without this foundational knowledge, identifying vulnerabilities, assessing risks, and implementing appropriate security controls becomes significantly more challenging. A well-defined asset and data inventory provides the necessary context for informed decision-making and proactive security management.
Cataloging Cloud Assets
A comprehensive asset inventory is the cornerstone of a robust cloud security posture. It allows organizations to know what they have, where it resides, and who has access to it. This knowledge is essential for incident response, compliance reporting, and overall risk management.To effectively catalog cloud assets, consider the following methods:
- Automated Discovery Tools: Utilize cloud provider-specific tools and third-party solutions to automatically discover and inventory assets. These tools can scan the cloud environment to identify virtual machines, storage accounts, databases, applications, and network configurations.
- Configuration Management Databases (CMDBs): Integrate cloud asset data with a CMDB to centralize asset information and provide a single source of truth. This integration allows for a more holistic view of the IT environment, including cloud assets.
- Cloud Provider APIs: Leverage cloud provider APIs to programmatically gather asset information. This approach allows for customized inventory solutions and the ability to retrieve real-time data.
- Infrastructure as Code (IaC) Tools: Use IaC tools like Terraform or AWS CloudFormation to manage infrastructure deployments. These tools can be used to track assets and their configurations, providing a consistent and auditable inventory.
- Regular Audits and Scans: Conduct regular audits and vulnerability scans to identify new assets and ensure the accuracy of the inventory. This helps to keep the inventory up-to-date and identify any unauthorized or misconfigured resources.
Categorizing Data Based on Sensitivity and Regulatory Requirements
Data classification is a crucial step in protecting sensitive information within the cloud. By categorizing data based on its sensitivity and regulatory requirements, organizations can prioritize security efforts and apply appropriate controls to protect their most valuable assets. This process helps to ensure compliance with relevant regulations and reduce the risk of data breaches.Data categorization typically involves the following steps:
- Identify Data Types: Determine the different types of data stored in the cloud, such as personally identifiable information (PII), financial data, intellectual property, and health information.
- Assess Sensitivity Levels: Assign sensitivity levels to each data type based on the potential impact of a data breach or unauthorized access. Common sensitivity levels include public, internal, confidential, and restricted.
- Map Data to Regulatory Requirements: Identify the regulatory requirements that apply to each data type, such as GDPR, HIPAA, PCI DSS, or CCPA.
- Document Data Classification Policy: Create a clear and concise data classification policy that defines the data types, sensitivity levels, regulatory requirements, and associated security controls.
- Implement Data Classification Tools: Utilize data loss prevention (DLP) tools and data classification tools to automate the data classification process and enforce security controls.
For example, a healthcare organization storing patient data in the cloud would classify this data as “Protected Health Information” (PHI) with a sensitivity level of “Restricted.” This data would be subject to HIPAA regulations, requiring specific security controls such as encryption, access controls, and audit logging.
Automating Asset Discovery and Inventory Management
Automating asset discovery and inventory management is critical for maintaining an accurate and up-to-date view of the cloud environment. Manual processes are time-consuming, error-prone, and unable to keep pace with the dynamic nature of cloud deployments. Automation ensures that asset information is readily available for security assessments, incident response, and compliance reporting.Here are some techniques for automating asset discovery and inventory management:
- Cloud Provider Native Tools: Utilize cloud provider-specific tools, such as AWS Config, Azure Resource Graph, or Google Cloud Asset Inventory, to automatically discover and track cloud resources. These tools provide real-time visibility into the cloud environment and can be configured to generate alerts for changes to assets.
- Third-Party Automation Tools: Implement third-party tools that integrate with multiple cloud providers and offer advanced features for asset discovery, inventory management, and vulnerability scanning. These tools can provide a centralized view of the cloud environment and automate security tasks.
- Infrastructure as Code (IaC): Leverage IaC tools to define and manage infrastructure as code. When infrastructure is deployed, these tools can automatically update the asset inventory with information about the new resources.
- API Integrations: Develop custom scripts or integrations that use cloud provider APIs to gather asset information and populate the inventory. This approach allows for highly customized asset discovery and inventory management solutions.
- Scheduled Scans: Schedule regular scans of the cloud environment to identify new assets, changes to existing assets, and any unauthorized resources. This ensures that the asset inventory is always up-to-date and accurate.
By automating asset discovery and inventory management, organizations can significantly improve their cloud security posture and reduce the risk of misconfigurations and vulnerabilities. This automation also streamlines security operations, enabling faster incident response and improved compliance reporting.
Threat Modeling and Vulnerability Identification
Threat modeling and vulnerability identification are crucial steps in cloud security risk assessments. They enable organizations to proactively understand potential threats, identify weaknesses in their cloud environment, and prioritize security efforts. This proactive approach helps mitigate risks before they can be exploited, enhancing the overall security posture.
Applying Threat Modeling Frameworks in a Cloud Context
Threat modeling frameworks provide a structured approach to identifying and analyzing potential threats. Several frameworks can be adapted for use in cloud environments.
The following are examples of frameworks and their applications:
- STRIDE: STRIDE (Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, Elevation of Privilege) is a threat modeling framework developed by Microsoft. In a cloud context, STRIDE helps identify threats related to authentication, data integrity, non-repudiation, information leakage, service availability, and unauthorized access. For instance, analyzing a cloud-based application using STRIDE could reveal potential vulnerabilities related to session hijacking (Spoofing), data corruption in a database (Tampering), or a lack of audit trails (Repudiation).
- PASTA: PASTA (Process for Attack Simulation and Threat Analysis) is a risk-centric threat modeling framework. PASTA focuses on understanding business objectives and mapping them to potential threats. It is useful for organizations that want to align their security efforts with their business goals. Using PASTA in a cloud environment helps identify threats based on the impact they could have on business operations, such as a denial-of-service attack that disrupts a critical cloud-hosted service.
Identifying Vulnerabilities Based on Cloud Provider Recommendations
Cloud providers offer security recommendations and best practices to help users secure their cloud environments. These recommendations provide valuable insights into potential vulnerabilities.
Consider the following points when identifying vulnerabilities based on cloud provider recommendations:
- Security Baselines: Cloud providers often publish security baselines, which are pre-configured security settings and configurations. These baselines provide a starting point for securing resources. Organizations can use these baselines to identify vulnerabilities in their current configurations.
- Configuration Best Practices: Cloud providers provide detailed documentation and best practices for configuring various cloud services. Following these recommendations helps reduce the attack surface. For example, AWS recommends using Multi-Factor Authentication (MFA) for all user accounts. Failure to implement MFA can lead to vulnerabilities.
- Regular Audits and Monitoring: Cloud providers offer tools for auditing and monitoring cloud resources. These tools can help identify misconfigurations, security breaches, and other vulnerabilities. For example, AWS CloudTrail logs API calls, which can be used to detect suspicious activity.
- Vulnerability Scanning: Cloud providers often integrate with or offer vulnerability scanning tools. These tools automatically scan resources for known vulnerabilities. These scans are critical for proactively identifying weaknesses.
Designing a Matrix to Map Threats to Vulnerabilities and Impact Levels
A matrix can be designed to map identified threats to corresponding vulnerabilities and assess their potential impact. This provides a clear overview of the risks and helps prioritize remediation efforts.
The matrix structure is designed to assist in risk prioritization. The columns include: Threat, Vulnerability, Impact Level (High, Medium, Low), and Mitigation Strategy. The rows will contain the specific threat, related vulnerability, impact level based on factors such as data sensitivity and business criticality, and a suggested mitigation strategy.
An example of such a matrix is presented below:
| Threat | Vulnerability | Impact Level | Mitigation Strategy |
|---|---|---|---|
| Account Compromise (e.g., credential theft) | Lack of Multi-Factor Authentication (MFA) | High | Implement MFA for all user accounts. Regularly review and rotate credentials. |
| Data Breach (e.g., unauthorized access to sensitive data) | Insecure Storage Configuration (e.g., publicly accessible storage buckets) | High | Configure storage buckets with appropriate access controls. Encrypt data at rest and in transit. Regularly audit storage configurations. |
| Denial of Service (DoS) Attack | Lack of DDoS Protection | Medium | Implement DDoS protection services. Monitor network traffic for unusual patterns. |
| Misconfiguration (e.g., overly permissive security group rules) | Insecure Network Configuration | Medium | Review and restrict security group rules. Implement a least-privilege access model. Regularly audit network configurations. |
| Malware Infection | Unpatched Operating Systems or Applications | High | Implement a patch management system. Regularly update operating systems and applications. Scan for malware. |
This matrix format allows for the easy identification of the most critical risks and provides a clear path for implementing mitigation strategies.
Risk Analysis and Prioritization
Risk analysis and prioritization is a critical phase in cloud security risk assessments. This process involves evaluating the potential impact and likelihood of identified risks, and then ranking them to determine which require immediate attention. This structured approach allows organizations to allocate resources effectively and mitigate the most significant threats first, enhancing their overall cloud security posture.
Assessing Likelihood and Impact
The assessment of risk likelihood and impact involves evaluating the probability of a threat exploiting a vulnerability and the potential consequences if it does. This process requires a systematic approach to ensure consistent and accurate evaluations.
- Determine the Likelihood of Occurrence: This involves assessing how probable it is that a threat will exploit a vulnerability. Factors to consider include the threat actor’s capabilities, the prevalence of the vulnerability, and the effectiveness of existing security controls.
- Evaluate the Impact of the Risk: The impact assessment determines the potential consequences if the risk materializes. This includes considering factors such as financial loss, reputational damage, legal and regulatory penalties, and operational disruption. Quantifying these impacts, where possible, provides a more objective assessment.
- Use a Consistent Rating Scale: Establish a standardized scale for both likelihood and impact. A common approach uses a numerical or qualitative scale (e.g., High, Medium, Low) to rate each factor. This ensures consistency across all risks.
- Gather Evidence and Data: Support the assessments with evidence, such as vulnerability scan results, threat intelligence reports, and historical data on past security incidents.
- Document the Rationale: Clearly document the reasons behind the likelihood and impact ratings. This documentation is crucial for justifying the risk assessment and for future reference.
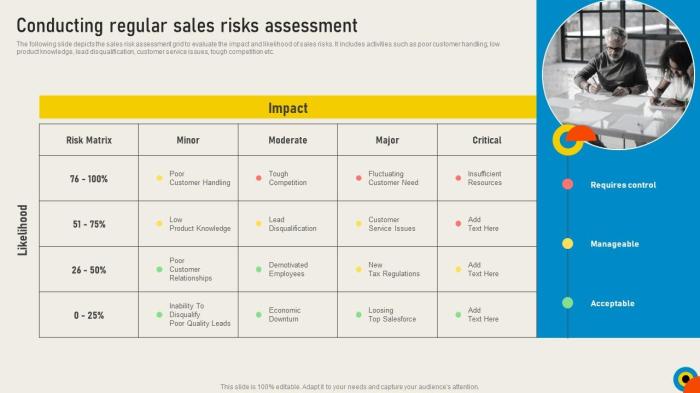
Using a Risk Matrix
A risk matrix is a valuable tool for prioritizing risks based on their severity. It visually represents the combination of likelihood and impact, enabling organizations to quickly identify and focus on the most critical risks.
A risk matrix typically uses a grid, with likelihood on one axis and impact on the other. The matrix is divided into zones or categories, such as High, Medium, and Low risk. The placement of a risk within the matrix indicates its priority.
Example of a Risk Matrix:
Imagine a 5×5 risk matrix where:
- Likelihood is rated from 1 (Very Low) to 5 (Very High).
- Impact is also rated from 1 (Very Low) to 5 (Very High).
The matrix cells are color-coded to represent risk levels:
- High Risk (Red): Risks with a high likelihood and high impact. These require immediate attention and mitigation.
- Medium Risk (Yellow): Risks with either a medium likelihood or medium impact, or a combination of both. These require planned mitigation efforts.
- Low Risk (Green): Risks with a low likelihood and low impact. These may require monitoring but may not need immediate action.
Example Scenario: A misconfigured cloud storage bucket (vulnerability) leading to a data breach (threat).
If the likelihood of exploitation is rated as 4 (High) and the impact is rated as 5 (Very High) due to potential financial penalties, reputational damage, and regulatory fines, the risk would fall into the High Risk (Red) category.
Documenting Risk Scores and Rationale
Thorough documentation is essential for maintaining a clear record of the risk assessment process, supporting decision-making, and facilitating future reviews. This documentation should include risk scores, the rationale behind the scores, and any relevant supporting information.
- Create a Risk Register: A risk register is a central repository for documenting all identified risks, their assessments, and mitigation plans. This document serves as a comprehensive record of the risk assessment process.
- Record Risk Scores: Document the likelihood and impact scores for each identified risk, using the established rating scales.
- Provide Rationale: Include a detailed explanation for each score. This should clearly state the reasons for assigning a particular likelihood and impact rating. The rationale should be based on evidence and supporting data.
- Include Mitigation Plans: Document the planned actions to address each identified risk, including the responsible parties, timelines, and resource allocation.
- Track Changes and Updates: Maintain a history of changes to the risk register, including dates, the individuals who made the changes, and the reasons for the updates.
- Regular Review: Regularly review and update the risk register to reflect changes in the threat landscape, the environment, and the effectiveness of existing controls.
Selecting and Implementing Security Controls
After identifying and assessing risks in your cloud environment, the next crucial step is to select and implement appropriate security controls. This process involves choosing the right measures to mitigate the identified risks, aligning these choices with industry best practices and standards. Effective implementation is paramount to ensuring the controls function as intended, providing the necessary protection for your cloud assets and data.
Choosing Security Controls
Selecting the right security controls is a risk-based process. The choice of controls should be directly tied to the identified risks and the potential impact of those risks. Industry standards and frameworks, such as the NIST Cybersecurity Framework, ISO 27001, and the Cloud Security Alliance (CSA) Cloud Controls Matrix (CCM), provide valuable guidance in this selection process. These frameworks offer a comprehensive set of controls that can be tailored to meet the specific needs of your organization and cloud environment.
Consider the following factors when selecting controls:
- Risk Severity: Prioritize controls that address the highest-impact risks.
- Control Effectiveness: Evaluate the effectiveness of each control in mitigating the identified risk.
- Cost-Benefit Analysis: Balance the cost of implementing and maintaining the control with its potential benefits in terms of risk reduction.
- Compliance Requirements: Ensure that the selected controls meet all relevant compliance requirements, such as GDPR, HIPAA, or PCI DSS.
- Cloud Provider Capabilities: Leverage the security features and services offered by your cloud provider.
Implementing Security Controls
Implementation involves deploying the selected controls and configuring them to meet your specific security requirements. The type of control and the chosen implementation method will vary depending on the nature of the risk being addressed. Effective implementation includes thorough documentation, ongoing monitoring, and regular testing to ensure controls are functioning correctly. The following are examples of how different control types can be implemented:
- Access Controls: Implement strong authentication and authorization mechanisms. This can involve multi-factor authentication (MFA), role-based access control (RBAC), and the principle of least privilege. For instance, in AWS, you can use IAM policies to define access permissions for users and groups.
- Encryption: Encrypt data at rest and in transit. This involves using encryption keys to protect sensitive data. Consider using cloud-provider-managed encryption services, such as AWS KMS or Azure Key Vault. For example, a company that uses encryption for its data in transit, such as a financial institution, reduces the risk of data breaches during the transfer of sensitive customer information.
- Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS): Deploy IDS/IPS solutions to monitor network traffic and detect malicious activity. Configure these systems to automatically block or alert on suspicious behavior. Cloud providers often offer managed IDS/IPS services as part of their security offerings.
- Vulnerability Scanning and Patch Management: Regularly scan your cloud infrastructure for vulnerabilities and apply security patches promptly. Utilize vulnerability scanning tools and automate the patch management process to ensure that systems are up-to-date and secure.
- Security Information and Event Management (SIEM): Implement a SIEM system to collect and analyze security logs from various sources. This allows for centralized security monitoring, threat detection, and incident response.
Security Controls Table
The following table illustrates examples of security controls, their types, implementation methods, and validation steps:
| Risk Addressed | Control Type | Implementation Method | Validation Steps |
|---|---|---|---|
| Unauthorized Access to Sensitive Data | Access Control | Implement Multi-Factor Authentication (MFA) and Role-Based Access Control (RBAC). Enforce the principle of least privilege. | Review user access logs, conduct periodic access reviews, and verify MFA implementation. Simulate access attempts to confirm restrictions. |
| Data Breach During Data Transfer | Encryption | Encrypt data in transit using TLS/SSL. Use cloud provider encryption services for data at rest. | Verify TLS/SSL configuration. Test data encryption and decryption. Confirm encryption key management practices. |
| Malware Infection | Intrusion Detection and Prevention | Deploy and configure an Intrusion Detection System (IDS) and Intrusion Prevention System (IPS). | Monitor IDS/IPS logs for alerts. Conduct penetration testing to simulate attacks and validate detection capabilities. Review and update rules regularly. |
| Exploitation of Vulnerabilities | Vulnerability Management | Implement vulnerability scanning and patch management processes. Regularly scan infrastructure and apply security patches. | Run vulnerability scans and review results. Verify patch deployment. Conduct penetration testing to confirm vulnerabilities are resolved. |
| Lack of Visibility and Threat Detection | Security Monitoring | Implement a Security Information and Event Management (SIEM) system to collect and analyze security logs. | Review SIEM dashboards and alerts. Conduct regular log analysis. Test incident response procedures. |
Testing and Validation of Security Controls
After implementing security controls, it’s crucial to verify their effectiveness. This involves rigorous testing and validation to ensure they function as intended and adequately mitigate identified risks. This phase provides assurance that the implemented controls are providing the intended level of protection for cloud assets and data.
Penetration Testing and Vulnerability Scanning for Security Control Effectiveness
Penetration testing and vulnerability scanning are vital techniques for assessing the effectiveness of implemented security controls. They simulate real-world attacks to identify weaknesses and confirm that controls are working as designed.Penetration testing involves simulating attacks to identify vulnerabilities that could be exploited by malicious actors. This process requires authorized attempts to breach security defenses.
- Penetration testers use various techniques, including:
- Information Gathering: Gathering information about the target system, including its architecture, services, and potential vulnerabilities. This helps in understanding the attack surface.
- Vulnerability Analysis: Identifying known vulnerabilities in the system’s software, hardware, and configurations. Testers use tools and manual analysis to discover these weaknesses.
- Exploitation: Attempting to exploit identified vulnerabilities to gain unauthorized access or achieve specific objectives. This step validates whether vulnerabilities can be successfully exploited.
- Post-Exploitation: Assessing the impact of successful exploitation, including the extent of access gained, data compromised, and potential damage. This helps determine the severity of the vulnerabilities.
Vulnerability scanning, on the other hand, automates the process of identifying vulnerabilities. This process is often automated, utilizing specialized tools that scan systems for known vulnerabilities.
- Vulnerability scanners typically:
- Scan for Known Vulnerabilities: These tools compare the target system’s software and configuration against a database of known vulnerabilities.
- Identify Misconfigurations: Scanners check for common misconfigurations that can lead to security breaches.
- Provide Reports: They generate detailed reports that Artikel the identified vulnerabilities, their severity, and recommended remediation steps.
Regularly scheduled penetration testing and vulnerability scanning are critical. Penetration testing is usually performed less frequently, often annually or biannually, while vulnerability scanning can be automated and performed more frequently, such as weekly or even daily, depending on the organization’s risk profile and the sensitivity of its data. The combination of both provides a comprehensive approach to security control validation.
For example, a company that handles sensitive financial data might perform penetration testing quarterly and run vulnerability scans daily to maintain a robust security posture.
Validating Control Configurations and Meeting Security Requirements
Validating control configurations is essential to ensure that implemented security controls are correctly configured and operating as intended. This involves verifying that the controls align with security requirements and industry best practices.Control configurations must align with security policies and regulatory requirements. For instance, if a company is subject to the Payment Card Industry Data Security Standard (PCI DSS), it must ensure that its access controls, encryption, and other security measures comply with PCI DSS requirements.
- Configuration validation often includes:
- Reviewing Configuration Settings: Examining the settings of security controls, such as firewalls, intrusion detection systems, and access control lists, to verify they are correctly configured.
- Testing Access Controls: Verifying that access controls are correctly implemented and that users have the appropriate levels of access.
- Verifying Encryption Settings: Confirming that encryption is properly configured for data at rest and in transit.
- Monitoring Security Logs: Reviewing security logs to detect any suspicious activity or anomalies that might indicate a control failure.
Configuration validation should be performed periodically and after any changes to the cloud environment. Automated configuration management tools can help to enforce security policies and ensure that configurations remain compliant over time. A financial institution, for example, might use an automated configuration management tool to ensure that all its cloud-based databases are configured with the latest security patches and encryption settings, thereby minimizing the risk of data breaches.
Documenting Testing and Validation Results
Proper documentation of testing and validation activities is essential for maintaining a clear record of security control effectiveness and for supporting compliance efforts. This documentation serves as evidence that the organization is actively managing its security risks.The documentation should include detailed records of all testing and validation activities. This provides a comprehensive overview of the security posture.
- Key elements of the documentation include:
- Testing Scope and Objectives: Clearly defining the scope of the testing, including the systems, applications, and data covered, as well as the specific security objectives being assessed.
- Testing Methodology: Describing the methods used for testing, such as penetration testing techniques or vulnerability scanning tools, and the specific tests performed.
- Findings and Results: Detailing the findings of the testing, including any identified vulnerabilities, misconfigurations, or weaknesses, along with their severity levels.
- Remediation Steps: Outlining the steps taken to remediate identified vulnerabilities, including the specific actions taken, the responsible parties, and the completion dates.
- Validation Results: Documenting the results of validation efforts, including confirmation that remediation steps were successful and that the controls are now functioning as intended.
- Dates and Version Control: Maintaining accurate dates and version control for all documentation to ensure it reflects the current state of the security controls.
This documentation is essential for compliance audits and security assessments. For example, a healthcare provider might need to provide documentation of its security testing and validation activities to demonstrate compliance with the Health Insurance Portability and Accountability Act (HIPAA). A well-documented process helps to demonstrate due diligence and supports the ongoing improvement of security controls.
Reporting and Communication of Findings
Effectively reporting and communicating the findings of a cloud security risk assessment is crucial for ensuring that identified risks are understood, prioritized, and addressed. This process involves creating clear, concise reports and tailoring communication to various stakeholders, both technical and non-technical, to facilitate informed decision-making and promote a proactive security posture.
Best Practices for Report Creation
Creating a comprehensive and easily digestible report is paramount to the success of a cloud security risk assessment. The report should accurately reflect the assessment’s findings, enabling stakeholders to grasp the identified risks and their implications. Adhering to best practices ensures clarity, conciseness, and actionable insights.
- Executive Summary: Begin with a brief overview of the assessment, its scope, and the key findings. This section should be easily understood by non-technical audiences, highlighting the most critical risks and their potential impact.
- Detailed Findings: Provide a thorough analysis of each identified risk, including its description, potential impact, likelihood, and severity. This section should include supporting evidence, such as vulnerability scans, configuration reviews, and threat modeling results.
- Risk Prioritization: Clearly rank risks based on their severity, considering both the likelihood of occurrence and the potential impact. Utilize a risk matrix or other visual aids to demonstrate the prioritization visually. For example, a risk with a high likelihood and high impact would be ranked as critical, while a risk with low likelihood and low impact would be ranked as low.
- Recommendations: Offer specific, actionable recommendations for mitigating each identified risk. These recommendations should be tailored to the organization’s specific cloud environment and security objectives. They should also include details such as the suggested security control, implementation steps, and estimated cost.
- Timeline and Responsibility: Include a proposed timeline for implementing the recommended security controls, along with the responsible parties. This promotes accountability and ensures that mitigation efforts are tracked and completed in a timely manner.
- Appendices: Include supporting documentation, such as detailed vulnerability reports, configuration checklists, and any other relevant information. This provides a comprehensive record of the assessment and allows for further investigation if needed.
Communicating Risk Findings to Stakeholders
Communicating risk findings effectively involves tailoring the message to the audience’s technical expertise and level of interest. This ensures that the information is understood and that stakeholders are motivated to take appropriate action. Effective communication can also build trust and collaboration between the security team and other departments.
- Technical Audiences: For technical audiences, such as IT staff and security engineers, focus on the technical details of the risks, including the vulnerabilities, attack vectors, and potential exploits. Provide detailed explanations of the findings, including specific technical details, and actionable recommendations.
- Non-Technical Audiences: For non-technical audiences, such as executives and business leaders, focus on the business impact of the risks. Explain the potential financial, reputational, and operational consequences of each risk. Use plain language, avoid technical jargon, and provide clear and concise summaries.
- Regular Updates: Provide regular updates on the progress of risk mitigation efforts. This keeps stakeholders informed and demonstrates the value of the security risk assessment.
- Visual Aids: Utilize visual aids, such as charts, graphs, and dashboards, to communicate complex information in a clear and concise manner. For instance, a risk matrix can visually represent the severity of risks, and a dashboard can track the progress of mitigation efforts.
- Training and Awareness: Provide training and awareness programs to educate employees about cloud security risks and best practices. This helps to create a security-conscious culture within the organization.
Security Risk Assessment Report Template
A well-structured report template can streamline the reporting process and ensure consistency across different assessments. The following template provides a framework for organizing and presenting the findings of a cloud security risk assessment.
| Section | Description | Example Content |
|---|---|---|
| 1. Executive Summary | A brief overview of the assessment, including the scope, key findings, and overall risk level. | “This report summarizes the findings of a cloud security risk assessment conducted on [Date] for [Organization Name]’s cloud environment. The assessment identified [Number] high-severity risks, including [Brief Description of Key Risks]. The overall risk level is assessed as [High/Medium/Low].” |
| 2. Introduction | Overview of the assessment’s purpose, scope, methodology, and assessment period. | “This document Artikels the findings of a comprehensive security risk assessment performed on [Cloud Provider] infrastructure used by [Organization Name]. The assessment covered [Specific Services/Applications] and was conducted using a combination of [Assessment Methodologies].” |
| 3. Scope and Methodology | Details about the scope of the assessment, including the systems, data, and services evaluated, and the methodologies used. | “The assessment scope included all services and data residing within the [Cloud Provider] environment, focusing on [Specific Areas, e.g., Compute Instances, Storage Buckets]. The methodology involved vulnerability scanning using [Tool Name], configuration reviews, and threat modeling.” |
| 4. Findings | Detailed findings, including descriptions of identified risks, their potential impact, likelihood, and severity. |
|
| 5. Risk Analysis and Prioritization | Prioritization of risks based on their severity and impact, often using a risk matrix. | “The identified risks were prioritized based on a risk matrix, considering both the likelihood of occurrence and the potential impact. [Include a risk matrix visual, with axes for likelihood and impact, and risks plotted accordingly]. High-severity risks include [List High-Severity Risks].” |
| 6. Recommendations | Specific, actionable recommendations for mitigating each identified risk. |
|
| 7. Conclusion | Summary of the assessment’s findings and recommendations. | “The cloud security risk assessment has identified several key vulnerabilities and potential threats. Implementing the recommended security controls will significantly reduce the organization’s overall risk posture. Continuous monitoring and regular assessments are recommended.” |
| 8. Appendices | Supporting documentation, such as vulnerability reports, configuration checklists, and any other relevant information. |
|
Remediation and Mitigation Strategies
Addressing identified risks is a critical step in the cloud security risk assessment process. This involves implementing strategies to reduce the likelihood and/or impact of potential threats. The goal is to bring the organization’s risk profile to an acceptable level. Effective remediation requires a systematic approach, encompassing the selection and implementation of appropriate controls, as well as a well-defined plan for execution.
Remediation Strategies for Addressing Identified Risks
Various remediation strategies can be employed to address identified risks in the cloud environment. The choice of strategy depends on the nature of the risk, the potential impact, and the organization’s risk tolerance.
- Patching: Applying security patches to address vulnerabilities in software and operating systems is a fundamental remediation strategy. This involves regularly updating software components, including the operating system, applications, and cloud services. Patching should be a continuous process, prioritizing critical vulnerabilities that could be exploited. For example, after the Log4j vulnerability was discovered in late 2021, organizations worldwide rushed to patch affected systems.
Failure to patch could have led to widespread exploitation and data breaches.
- Configuration Changes: Incorrect or insecure configurations are a common source of cloud security vulnerabilities. Remediation often involves modifying configurations to align with security best practices and organizational policies. This might include:
- Strengthening access controls (e.g., implementing multi-factor authentication, least privilege).
- Disabling unnecessary services.
- Configuring network security controls (e.g., firewalls, intrusion detection systems).
- Regularly reviewing and updating configurations.
- Process Improvements: Improving internal processes can significantly enhance cloud security posture. This includes:
- Implementing robust change management processes to ensure that changes to the cloud environment are properly reviewed and authorized.
- Developing and enforcing security policies and standards.
- Conducting regular security awareness training for employees.
- Establishing incident response plans to handle security breaches effectively.
- Implementation of Security Controls: Selecting and deploying security controls to mitigate identified risks. Examples include:
- Access Control: Implementing robust access control mechanisms, such as multi-factor authentication (MFA) and role-based access control (RBAC), to limit access to sensitive data and resources.
- Encryption: Encrypting data at rest and in transit to protect its confidentiality. This can be achieved through the use of encryption keys and protocols.
- Intrusion Detection and Prevention Systems (IDPS): Deploying IDPS to monitor network traffic and identify malicious activity. These systems can alert security teams to potential threats and block malicious traffic.
- Web Application Firewalls (WAF): Using WAFs to protect web applications from common attacks, such as cross-site scripting (XSS) and SQL injection.
- Risk Acceptance: In some cases, the cost of mitigating a risk may outweigh the potential impact. In these situations, the organization may choose to accept the risk, but this decision should be made consciously and with proper documentation. Risk acceptance often requires monitoring the accepted risk and regularly reevaluating it.
Developing a Remediation Plan
A well-defined remediation plan is essential for effectively addressing identified risks. The plan should Artikel the specific actions to be taken, the timelines for completion, and the responsible parties.
- Risk Prioritization: The remediation plan should prioritize risks based on their severity and potential impact. Risks with the highest priority should be addressed first.
- Action Items: Each risk should be associated with specific action items, such as applying a patch, changing a configuration setting, or implementing a new security control.
- Timelines: Realistic timelines should be established for completing each action item. These timelines should consider factors such as the complexity of the task, the availability of resources, and the urgency of the risk.
- Responsible Parties: Assigning clear responsibility for each action item is crucial. This ensures accountability and facilitates tracking progress.
- Resources: Identify the resources required to implement the remediation plan, including personnel, tools, and budget.
- Tracking and Reporting: Establish a system for tracking progress and reporting on the status of the remediation plan. This might involve using a project management tool or creating regular status reports.
Example Remediation Plan Snippet:
| Risk ID | Risk Description | Action Item | Timeline | Responsible Party | Status |
|---|---|---|---|---|---|
| RISK-001 | Unpatched Web Server | Apply Security Patch (CVE-2023-XXXX) | 7 days | System Administrator | In Progress |
| RISK-002 | Weak Password Policy | Enforce Stronger Password Requirements | 30 days | Security Team | Not Started |
Remediation Workflow Flowchart
The following flowchart illustrates the typical remediation workflow, from risk identification to resolution.
Flowchart Description:
The flowchart begins with “Risk Identification” which is the starting point. After risk identification, the process flows to “Risk Assessment” where the risks are analyzed and prioritized. Then, the flowchart branches into “Remediation Planning,” where remediation strategies are developed, and “Control Implementation,” where selected security controls are deployed. Both branches converge at “Implementation Verification,” which involves testing and validation of the implemented controls and the effectiveness of the remediation plan.
If the remediation is successful, the process moves to “Risk Acceptance” or “Risk Mitigation” (if the risk is mitigated), and finally, the flowchart concludes with “Ongoing Monitoring,” where the cloud environment is continuously monitored to ensure that risks remain at an acceptable level. If the remediation is unsuccessful, the process returns to “Remediation Planning” to refine the strategy.
Continuous Monitoring and Review
Continuous monitoring and review are critical components of a robust cloud security risk assessment program. They ensure that the implemented security controls remain effective over time, that new threats and vulnerabilities are identified and addressed promptly, and that the overall security posture of the cloud environment is maintained. Regular monitoring and review provide valuable insights into the effectiveness of security measures and enable proactive adjustments to mitigate evolving risks.
Importance of Ongoing Monitoring for Incident Detection and Response
Ongoing monitoring is essential for detecting and responding to security incidents. This involves actively tracking various aspects of the cloud environment to identify anomalies, suspicious activities, and potential security breaches. Effective monitoring systems provide real-time visibility into the environment, allowing for rapid detection and response to threats.To achieve effective incident detection and response, consider the following:
- Implement Real-Time Monitoring Tools: Deploy tools that continuously monitor cloud resources, network traffic, and user activity. These tools should be capable of generating alerts based on predefined rules and thresholds. For example, security information and event management (SIEM) systems aggregate and analyze security logs from various sources to detect suspicious patterns.
- Establish Baseline Behavior: Define a baseline of normal activity for the cloud environment. This baseline helps identify deviations that may indicate malicious activity. Machine learning algorithms can be used to automatically learn and adapt to the normal behavior of the system, reducing the number of false positives.
- Define Incident Response Procedures: Develop and document clear incident response procedures that Artikel the steps to be taken when a security incident is detected. This should include roles and responsibilities, communication protocols, and escalation procedures. Regular testing of these procedures through tabletop exercises or simulations is crucial.
- Utilize Threat Intelligence Feeds: Integrate threat intelligence feeds to stay informed about the latest threats, vulnerabilities, and attack techniques. This information can be used to update security rules, identify potential threats, and proactively defend against attacks.
- Implement Automated Alerting and Notification: Configure automated alerts and notifications to notify the appropriate personnel when security incidents are detected. This ensures that incidents are addressed promptly and efficiently.
Establishing a Process for Regular Review of Security Controls and Risk Assessments
Establishing a structured process for regularly reviewing security controls and risk assessments is essential for maintaining a strong security posture. This process ensures that the effectiveness of security controls is validated, risk assessments are updated to reflect changes in the environment and threat landscape, and necessary adjustments are made to mitigate emerging risks.The review process should include the following key elements:
- Define Review Frequency: Determine how often security controls and risk assessments will be reviewed. The frequency should be based on factors such as the criticality of the assets, the rate of change in the environment, and the evolving threat landscape. Generally, reviews should be conducted at least annually, but more frequent reviews may be necessary for high-risk environments.
- Establish a Review Team: Assemble a team responsible for conducting the reviews. The team should include individuals with expertise in cloud security, risk management, and relevant technical areas. It’s important to include representatives from various departments, such as IT operations, security, and business units.
- Document the Review Process: Create a documented process that Artikels the steps involved in conducting the reviews. This process should include the scope of the review, the data sources to be used, the review methodology, and the reporting requirements.
- Conduct a Gap Analysis: Compare the current state of security controls and risk assessments with the desired state. Identify any gaps or deficiencies that need to be addressed.
- Prioritize Remediation Activities: Based on the findings of the review, prioritize remediation activities. This prioritization should be based on the severity of the risks, the potential impact of the vulnerabilities, and the feasibility of implementing the remediation measures.
- Track Remediation Progress: Monitor the progress of remediation activities to ensure that they are completed in a timely manner. Regular follow-up and reporting are essential to ensure accountability and track the effectiveness of the remediation efforts.
- Update Risk Assessments: Revise risk assessments based on the findings of the review. This includes updating the risk ratings, updating the likelihood and impact of potential threats, and identifying any new risks that have emerged.
Checklist for Continuous Monitoring Activities
A well-defined checklist can ensure that all necessary aspects of continuous monitoring are covered. This checklist should be regularly reviewed and updated to reflect changes in the cloud environment, security threats, and organizational policies.Here is a sample checklist for continuous monitoring activities:
- Log Collection and Analysis:
- Ensure all relevant logs are being collected from cloud resources, applications, and network devices.
- Implement a centralized log management system for efficient analysis.
- Establish automated log analysis rules to detect suspicious activities and security events.
- Regularly review and update log retention policies.
- Vulnerability Scanning:
- Schedule regular vulnerability scans of cloud resources.
- Utilize vulnerability scanning tools to identify known vulnerabilities.
- Prioritize vulnerabilities based on their severity and potential impact.
- Track and remediate identified vulnerabilities in a timely manner.
- Configuration Monitoring:
- Monitor the configuration of cloud resources to ensure compliance with security policies and best practices.
- Detect and alert on any unauthorized configuration changes.
- Implement automated configuration management tools.
- Regularly review and update configuration baselines.
- Network Monitoring:
- Monitor network traffic for suspicious activity, such as unauthorized access attempts or data exfiltration.
- Utilize intrusion detection and prevention systems (IDS/IPS).
- Analyze network traffic patterns to identify anomalies.
- Review and update network security rules.
- User Activity Monitoring:
- Monitor user activity to detect unauthorized access, privilege escalation, and other suspicious behavior.
- Implement user behavior analytics (UBA) tools.
- Review user access logs regularly.
- Conduct regular access reviews to ensure appropriate access controls.
- Security Incident Response:
- Establish and test incident response plans.
- Monitor security alerts and respond to incidents promptly.
- Document all security incidents and their resolution.
- Conduct post-incident analysis to identify root causes and prevent future incidents.
- Compliance Monitoring:
- Monitor compliance with relevant security standards and regulations.
- Utilize compliance monitoring tools.
- Generate compliance reports regularly.
- Address any compliance gaps promptly.
Cloud Provider Specific Considerations
Understanding the nuances of cloud provider security is crucial for a comprehensive risk assessment. Each major provider, Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP), offers a unique set of services, configurations, and security controls. A robust risk assessment process must incorporate these provider-specific aspects to accurately identify and mitigate potential vulnerabilities. Neglecting these considerations can lead to significant security gaps.
Unique Security Considerations for AWS, Azure, and GCP
Each cloud provider presents distinct security considerations due to their architectural differences, service offerings, and shared responsibility models. Focusing on these specific areas is critical for a successful risk assessment.
- Amazon Web Services (AWS): AWS has a vast and mature ecosystem, offering a wide array of services. Security considerations include:
- Identity and Access Management (IAM): Managing IAM roles, policies, and users is critical. Overly permissive IAM policies can lead to unauthorized access. AWS recommends using the principle of least privilege.
- Security Groups and Network Access Control Lists (NACLs): Configuring these network controls correctly is essential for segmenting and protecting resources. Misconfigurations can expose resources to the internet.
- Key Management Service (KMS) and Encryption: AWS KMS allows for the creation and management of encryption keys. Ensuring proper key rotation and access control is vital for data protection.
- AWS Config and CloudTrail: These services provide configuration tracking and audit logging. Regular review of these logs is necessary to detect and respond to security incidents.
- Shared Responsibility Model: AWS is responsible for the security
-of* the cloud, while the customer is responsible for the security
-in* the cloud. This includes data protection, IAM, and security configurations. - Microsoft Azure: Azure offers a comprehensive set of services tightly integrated with Microsoft’s ecosystem. Security considerations include:
- Azure Active Directory (Azure AD): Azure AD is the identity and access management service. Securing Azure AD accounts and implementing multi-factor authentication (MFA) are paramount.
- Network Security Groups (NSGs) and Azure Firewall: Azure offers NSGs for basic network filtering and Azure Firewall for more advanced threat protection. Proper configuration is crucial.
- Azure Key Vault: Azure Key Vault provides secure storage for secrets, keys, and certificates. Implementing strong access controls and monitoring are essential.
- Azure Security Center and Azure Sentinel: These services provide security monitoring, threat detection, and incident response capabilities. Utilizing these services is crucial for maintaining a strong security posture.
- Shared Responsibility Model: Similar to AWS, Azure operates under a shared responsibility model. Microsoft secures the underlying infrastructure, while customers are responsible for their data and configurations.
- Google Cloud Platform (GCP): GCP emphasizes data analytics, machine learning, and containerization. Security considerations include:
- Cloud Identity and Access Management (Cloud IAM): Cloud IAM provides granular access control. Implementing the principle of least privilege is essential to minimize the attack surface.
- Virtual Private Cloud (VPC) and Firewall Rules: Configuring VPC networks and firewall rules correctly is critical for network segmentation and protection.
- Cloud Key Management Service (Cloud KMS): Cloud KMS enables you to manage cryptographic keys. Proper key management and access control are vital for data protection.
- Cloud Security Command Center (Cloud SCC): Cloud SCC provides a centralized view of security findings, asset inventory, and threat detection. Regularly reviewing findings is crucial.
- Shared Responsibility Model: GCP operates under a shared responsibility model, similar to AWS and Azure. Google secures the infrastructure, and customers are responsible for their data and configurations.
Comparison of Security Services
Each cloud provider offers a suite of security services. Comparing these services helps in making informed decisions during the risk assessment process. This comparison helps to highlight the strengths and weaknesses of each provider.
| Feature | AWS | Azure | GCP |
|---|---|---|---|
| Identity and Access Management | IAM (Roles, Policies) | Azure AD (Roles, RBAC) | Cloud IAM (Roles, Policies) |
| Network Security | Security Groups, NACLs, AWS Firewall Manager | NSGs, Azure Firewall | VPC, Firewall Rules, Cloud Armor |
| Key Management | KMS | Key Vault | Cloud KMS |
| Security Monitoring/SIEM | CloudTrail, CloudWatch, Security Hub, Amazon Detective | Security Center, Sentinel | Cloud SCC, Chronicle Security |
| Vulnerability Scanning | Amazon Inspector | Microsoft Defender for Cloud | Security Command Center |
Incorporating Provider-Specific Security Recommendations
Integrating provider-specific security recommendations is a critical part of a robust risk assessment. This process ensures the assessment aligns with best practices and minimizes risks specific to the chosen cloud environment.
- Review Provider Documentation: The first step is to thoroughly review the security documentation provided by each cloud provider. These documents offer specific recommendations and best practices.
- Use Security Benchmarks: Utilize security benchmarks like the CIS Benchmarks for AWS, Azure, and GCP. These benchmarks provide a standardized approach to security configuration and assessment.
- Leverage Provider-Specific Security Tools: Integrate provider-specific security tools into the risk assessment process. For example, use AWS Security Hub, Azure Security Center, or GCP’s Security Command Center to identify vulnerabilities and misconfigurations.
- Consider Service-Specific Risks: When assessing risks, consider the specific services used within each cloud environment. For example, assess the security of Amazon S3 buckets, Azure Blob storage, or Google Cloud Storage.
- Automate Security Assessments: Automate security assessments using tools that integrate with each cloud provider’s APIs. This will ensure consistent and frequent assessments.
- Stay Updated: Cloud providers continuously update their services and security recommendations. Regularly update the risk assessment process to reflect these changes.
Final Summary
In conclusion, mastering the steps for conducting regular cloud security risk assessments is not merely a technical exercise; it’s a strategic imperative. By embracing a proactive, systematic approach, organizations can fortify their cloud environments, minimize vulnerabilities, and maintain the trust of their stakeholders. Continuous vigilance, regular reviews, and adaptation to the ever-changing threat landscape are key to ensuring the long-term security and success of your cloud initiatives.
This comprehensive guide serves as a foundation for building a secure and resilient cloud infrastructure, allowing you to harness the full potential of cloud technology with confidence.
Helpful Answers
What is the frequency of cloud security risk assessments?
Regular cloud security risk assessments should be conducted at least annually, or more frequently if there are significant changes to the cloud environment, new threats emerge, or regulatory requirements evolve. The frequency can also be determined based on the criticality of the data and applications hosted in the cloud.
How do I prioritize risks identified during the assessment?
Prioritize risks based on their potential impact and likelihood of occurrence. Use a risk matrix to categorize risks based on severity, allowing you to focus remediation efforts on the most critical vulnerabilities first. Consider factors such as data sensitivity, business impact, and regulatory compliance.
What are the key components of a cloud security risk assessment report?
A cloud security risk assessment report should include an executive summary, scope definition, asset inventory, identified threats and vulnerabilities, risk analysis and prioritization, security control recommendations, remediation plan, and a conclusion with recommendations for continuous improvement. It should be clear, concise, and tailored to both technical and non-technical audiences.
How can automation assist in cloud security risk assessments?
Automation can significantly streamline cloud security risk assessments. Tools can automate asset discovery, vulnerability scanning, configuration audits, and compliance checks. Automating these tasks reduces manual effort, improves accuracy, and allows for more frequent assessments, leading to a more robust security posture.