In today’s digital landscape, safeguarding an organization’s assets from cyber threats is paramount. This is where a Security Operations Center (SOC) steps in, acting as a vigilant guardian against evolving cyberattacks. A SOC is more than just a team; it’s a strategic approach to cybersecurity, constantly monitoring, analyzing, and responding to security incidents. This guide will delve into the intricate world of a SOC, exploring the diverse roles, responsibilities, and technologies that contribute to its effectiveness.
From the front-line Security Analysts to the strategic SOC Managers, each role plays a crucial part in defending against threats. We’ll explore the structure of a typical SOC, examining how different teams, such as Incident Response and Threat Intelligence, collaborate to protect an organization. Furthermore, we’ll examine the tools and technologies that enable SOC teams to detect, analyze, and respond to incidents efficiently, and discuss the importance of communication and collaboration in a successful SOC environment.
Overview of a Security Operations Center (SOC)
A Security Operations Center (SOC) is a centralized function within an organization that employs a team of cybersecurity professionals to monitor, detect, analyze, and respond to cybersecurity incidents. The SOC serves as the central hub for all security-related activities, ensuring the protection of an organization’s digital assets.
Primary Purpose of a SOC
The primary purpose of a SOC is to protect an organization’s information assets by proactively identifying and mitigating cybersecurity threats. This involves a combination of technologies, processes, and people working together to maintain a strong security posture. The SOC’s role extends beyond simply reacting to incidents; it also focuses on prevention and continuous improvement of security measures.
Significance of a SOC in Modern Cybersecurity Strategies
In today’s complex threat landscape, a SOC is a critical component of any robust cybersecurity strategy. Organizations face a constant barrage of sophisticated attacks, including malware, ransomware, phishing, and insider threats. Without a dedicated SOC, organizations are significantly more vulnerable to these attacks. The SOC provides:
- 24/7 Monitoring: Continuous monitoring of network traffic, endpoints, and other systems allows for rapid detection of suspicious activity.
- Incident Response: A structured process for responding to and mitigating security incidents, minimizing damage and downtime.
- Threat Intelligence: Integration of threat intelligence feeds to stay informed about the latest threats and vulnerabilities.
- Proactive Security: Analysis of security data to identify vulnerabilities and implement preventative measures.
Core Objectives of a SOC
A SOC has several core objectives, all focused on protecting the organization’s data and systems. These objectives guide the SOC’s activities and help ensure its effectiveness. These are the main objectives:
- Detection: Identify potential security incidents through continuous monitoring and analysis of security data.
- Analysis: Investigate and analyze security alerts to determine the nature and severity of incidents.
- Containment: Limit the impact of security incidents by isolating affected systems and preventing further damage.
- Eradication: Remove the root cause of security incidents, such as malware or compromised accounts.
- Recovery: Restore affected systems and data to their normal operating state.
- Prevention: Proactively identify and address vulnerabilities to prevent future incidents.
- Improvement: Continuously improve security processes and technologies based on lessons learned from incidents.
SOC Team Structure and Hierarchy
Understanding the organizational structure of a Security Operations Center (SOC) is crucial for its operational efficiency and effectiveness. A well-defined structure ensures clear lines of communication, streamlined workflows, and a coordinated approach to cybersecurity threats. This section will explore a typical SOC team structure, outlining the various roles, their reporting lines, and the relationships between different teams within the SOC.
SOC Team Structure
A typical SOC team structure is hierarchical, designed to provide clear reporting lines and facilitate efficient decision-making. This structure allows for the delegation of responsibilities and the specialization of skills, enabling the SOC to effectively address a wide range of security incidents and threats. The specific structure can vary based on the size and needs of the organization, but a common model includes the following roles and reporting relationships.
SOC Team Member Responsibilities
The SOC team is composed of individuals with specialized skills and responsibilities. These responsibilities are often organized to ensure comprehensive coverage of security threats and efficient incident response. The following table details the primary roles within a SOC, their key responsibilities, and the reporting lines within the organization.“`html
| Role | Responsibilities | Reporting Line | Key Skills |
|---|---|---|---|
| SOC Manager | Oversees the entire SOC operation, including team performance, budget management, and strategic planning. Ensures alignment with organizational security goals. | Reports to the CISO (Chief Information Security Officer) or equivalent. | Leadership, strategic thinking, risk management, communication, and project management. |
| Security Analyst (Tier 1) | Monitors security alerts, performs initial triage of incidents, and escalates complex issues to higher-tier analysts. Conducts basic investigations and supports incident response. | Reports to the SOC Manager or a Team Lead. | SIEM tools, basic network security, threat detection, and incident handling. |
| Security Analyst (Tier 2) | Conducts in-depth investigations of security incidents, performs malware analysis, and develops incident response plans. Provides guidance to Tier 1 analysts. | Reports to the SOC Manager or a Team Lead. | Advanced threat analysis, malware analysis, forensic analysis, incident response, and vulnerability assessment. |
| Threat Intelligence Analyst | Gathers, analyzes, and disseminates threat intelligence to inform security strategies and improve detection capabilities. Monitors threat actors, vulnerabilities, and emerging threats. | Reports to the SOC Manager or a Team Lead. | Threat intelligence platforms, threat modeling, vulnerability research, and security research. |
| Incident Responder | Leads the response to security incidents, including containment, eradication, and recovery efforts. Coordinates with other teams to mitigate and resolve incidents. | Reports to the SOC Manager or a Team Lead. | Incident response methodologies, digital forensics, and communication skills. |
| Security Engineer | Designs, implements, and maintains security tools and infrastructure. Automates security processes and provides technical expertise to the SOC team. | Reports to the SOC Manager or a Team Lead. | Security tool administration, network security, system administration, and automation. |
“`
Relationships Between SOC Teams
Effective collaboration between different teams within the SOC is crucial for its overall success. The relationships between teams, such as Incident Response and Threat Intelligence, are essential for a coordinated and proactive approach to cybersecurity.
- Incident Response and Security Analysts: Incident responders rely on security analysts to identify and escalate potential security incidents. They work closely to validate alerts, investigate incidents, and implement containment and remediation strategies. Security analysts provide the initial analysis, while incident responders take the lead in managing the incident.
- Threat Intelligence and Security Analysts: Threat Intelligence provides the security analysts with the context needed to understand threats. This includes information about threat actors, tactics, techniques, and procedures (TTPs), and indicators of compromise (IOCs). Security analysts use this information to improve their detection capabilities and proactively hunt for threats.
- Incident Response and Threat Intelligence: Incident responders provide feedback to the Threat Intelligence team on the effectiveness of current security measures and the evolving threat landscape. This information helps the Threat Intelligence team refine their analysis and develop new defenses. For example, a successful phishing attack might prompt Threat Intelligence to research the specific tactics used and update security awareness training.
- Security Engineers and all other Teams: Security engineers provide the technical infrastructure and tools necessary for the SOC to function. They work with all other teams to implement and maintain security solutions, automate processes, and improve the overall security posture. They support the other teams by configuring security tools and systems.
Security Analyst Roles and Responsibilities
Security Analysts are the frontline defenders in a Security Operations Center (SOC), playing a critical role in detecting, analyzing, and responding to security incidents. Their responsibilities are multifaceted and require a blend of technical expertise, analytical skills, and a proactive approach to cybersecurity. They are essential for maintaining the security posture of an organization.
Daily Tasks and Duties of a Level 1 Security Analyst
Level 1 Security Analysts are typically the first responders to security alerts and incidents. They perform a variety of daily tasks to ensure the smooth operation of the SOC and the protection of the organization’s assets.
- Monitoring Security Systems: This involves constantly reviewing security dashboards, logs, and alerts generated by various security tools, such as Security Information and Event Management (SIEM) systems, intrusion detection/prevention systems (IDS/IPS), and endpoint detection and response (EDR) solutions. This continuous monitoring is crucial for identifying potential threats and anomalies.
- Alert Triage and Initial Analysis: Upon receiving an alert, Level 1 analysts triage the alert to determine its severity and potential impact. This involves investigating the alert’s context, such as the affected asset, the nature of the activity, and any associated indicators of compromise (IOCs).
- Incident Escalation: If an alert warrants further investigation or requires specialized expertise, the Level 1 analyst escalates the incident to a Level 2 or Level 3 analyst. This escalation process ensures that complex or high-impact incidents are handled by personnel with the appropriate skills and experience.
- Documentation and Reporting: Maintaining accurate and detailed documentation of all activities, including alerts, investigations, and escalations, is a crucial aspect of the Level 1 analyst’s role. This documentation is essential for tracking incidents, providing evidence for investigations, and improving security processes.
- Basic Malware Analysis: Level 1 analysts often perform initial malware analysis, which may involve examining suspicious files, identifying malicious code, and determining the malware’s potential impact. This analysis can help in understanding the nature of the threat and formulating an appropriate response.
- User Support and Training: Providing support to end-users regarding security-related issues, such as phishing attempts or suspicious emails, is another important duty. They may also assist in training users on security best practices.
Incident Investigation Methodologies Employed
Level 1 Security Analysts utilize specific methodologies to investigate security incidents, ensuring a systematic and thorough approach.
- Alert Verification: This initial step involves confirming the validity of the alert. This includes verifying the source, the affected systems, and the specific events that triggered the alert.
- Contextualization: Gathering context around the alert is crucial. This includes identifying the affected asset, the user involved, the type of activity, and any relevant environmental factors. Understanding the context helps in determining the potential impact of the incident.
- Initial Containment: Implementing immediate containment measures to limit the scope of the incident is often necessary. This may involve isolating affected systems, blocking malicious traffic, or disabling compromised accounts.
- Evidence Gathering: Collecting relevant evidence to support the investigation is essential. This can include log files, network traffic captures, and system snapshots.
- Analysis of IOCs: Identifying and analyzing Indicators of Compromise (IOCs), such as malicious IP addresses, domain names, and file hashes, is a key part of the investigation. This analysis helps in understanding the nature of the threat and identifying other potentially affected systems.
- Documentation: Throughout the investigation, all actions taken, findings, and evidence gathered are meticulously documented. This documentation serves as a record of the investigation and is critical for reporting and future analysis.
Tools and Technologies Utilized
Level 1 Security Analysts rely on a variety of tools and technologies to perform their duties effectively.
- SIEM Systems: Security Information and Event Management (SIEM) systems are central to the SOC, aggregating logs from various sources and providing a centralized view of security events. Examples include Splunk, QRadar, and ArcSight.
- Endpoint Detection and Response (EDR) Solutions: EDR solutions provide real-time monitoring and response capabilities for endpoints, such as computers and servers. They help in detecting and responding to threats on individual devices. Examples include CrowdStrike Falcon, Microsoft Defender for Endpoint, and SentinelOne.
- Intrusion Detection/Prevention Systems (IDS/IPS): These systems monitor network traffic for malicious activity and can automatically block or alert on suspicious behavior.
- Vulnerability Scanners: Tools like Nessus and OpenVAS are used to identify vulnerabilities in systems and applications.
- Network Monitoring Tools: These tools, such as Wireshark and tcpdump, are used to analyze network traffic and identify suspicious activity.
- Threat Intelligence Feeds: Security analysts use threat intelligence feeds from sources like Recorded Future and VirusTotal to stay informed about the latest threats and IOCs.
- Ticketing Systems: These systems, such as ServiceNow and Jira, are used to track incidents, manage workflows, and facilitate communication.
- Basic Malware Analysis Tools: Tools like VirusTotal, online sandbox environments, and basic static analysis tools are used to analyze suspicious files.
Incident Response Team Roles and Responsibilities
The Incident Response (IR) team is a critical component of the Security Operations Center (SOC). Their primary responsibility is to handle security incidents effectively, minimizing damage, and restoring normal operations as quickly as possible. This involves a structured approach, well-defined procedures, and seamless coordination with other departments.
Incident Response Lead Responsibilities
The Incident Response Lead is the central figure responsible for the overall management and execution of the incident response process. They provide leadership, guidance, and strategic direction during security incidents. Their responsibilities include the following:
- Incident Coordination and Management: The IR Lead oversees all aspects of incident handling, from initial detection and assessment to containment, eradication, and recovery. They ensure that all team members are aware of their roles and responsibilities and that the incident response plan is followed.
- Team Leadership and Mentorship: They provide guidance and support to the IR team members, fostering a collaborative and effective working environment. They also mentor junior team members, helping them develop their skills and expertise.
- Communication and Reporting: The IR Lead is responsible for communicating with stakeholders, including senior management, legal counsel, public relations, and potentially external parties such as law enforcement or regulatory bodies. They provide regular updates on the incident’s progress and impact.
- Incident Response Plan Development and Maintenance: They are responsible for developing, reviewing, and updating the incident response plan to ensure it remains current and effective. This includes incorporating lessons learned from past incidents and adapting to changes in the threat landscape.
- Resource Allocation: They allocate resources, including personnel, tools, and budget, to support the incident response efforts. They ensure that the team has the necessary resources to effectively handle incidents.
- Post-Incident Analysis and Reporting: After an incident is resolved, the IR Lead leads the post-incident analysis to identify the root cause, assess the effectiveness of the response, and recommend improvements to prevent future incidents. They then prepare a comprehensive report documenting the incident and the response efforts.
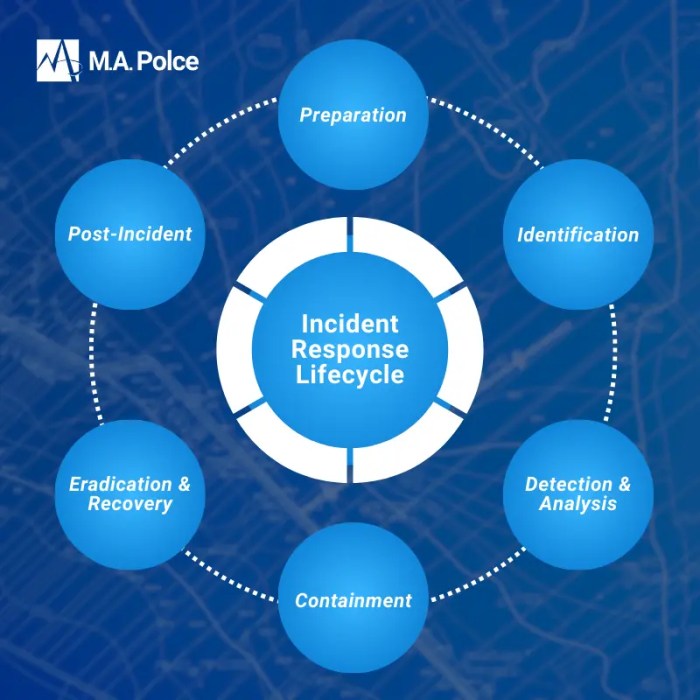
Incident Handling Procedures
Incident handling follows a structured, phased approach to ensure a systematic and effective response. These phases are generally categorized as follows:
- Preparation: This phase involves establishing the necessary infrastructure, policies, and procedures to handle security incidents effectively. This includes developing an incident response plan, training the incident response team, and implementing security tools and technologies.
- Identification: This phase involves detecting and identifying security incidents. This can be achieved through various methods, including security monitoring, log analysis, vulnerability scanning, and threat intelligence.
- Containment: Once an incident is identified, the primary goal is to contain the damage and prevent further spread. This involves taking immediate actions to isolate the affected systems or networks. Examples of containment measures include isolating infected systems, disabling compromised accounts, and blocking malicious traffic.
- Eradication: After containment, the next step is to eradicate the threat. This involves removing the root cause of the incident and eliminating any malicious software or activity. This may include removing malware, patching vulnerabilities, and restoring compromised systems from clean backups.
- Recovery: This phase focuses on restoring affected systems and services to their normal operational state. This may involve restoring data from backups, reconfiguring systems, and verifying that the incident has been fully resolved.
- Post-Incident Activity: After the incident is resolved, the team conducts a post-incident analysis to identify the root cause of the incident, assess the effectiveness of the response, and recommend improvements to prevent future incidents. This includes documenting the incident, analyzing the data, and developing a lessons-learned report.
Coordination with Other Departments
Effective incident response requires seamless coordination with other departments within the organization. This ensures that the response is comprehensive and that all relevant stakeholders are informed and involved. Here’s how the Incident Response team typically coordinates with other departments:
- IT Operations: The IR team works closely with IT Operations to contain and eradicate threats, restore affected systems, and implement security patches. This collaboration is crucial for the technical aspects of incident handling, such as system isolation, data recovery, and infrastructure restoration.
- Legal Department: The IR team collaborates with the legal department to ensure compliance with legal and regulatory requirements. This includes reporting incidents to relevant authorities, preserving evidence, and handling legal matters related to the incident. For example, in the case of a data breach involving Personally Identifiable Information (PII), the legal team would be involved in notifying affected individuals and complying with data privacy regulations like GDPR or CCPA.
- Public Relations: The IR team coordinates with the public relations department to manage communications with the public and media during and after an incident. This ensures that the organization’s messaging is consistent and that any reputational damage is minimized. A real-world example would be a ransomware attack where PR would craft statements and address public concerns.
- Human Resources: In cases involving employee misconduct or insider threats, the IR team works with Human Resources to address personnel-related issues. This may involve disciplinary actions, investigations, and employee training.
- Executive Management: The IR Lead reports to executive management, providing updates on the incident’s progress, impact, and any potential risks to the organization. This communication is critical for ensuring that senior leadership is aware of the situation and can make informed decisions.
- Physical Security: In cases involving physical security breaches, such as unauthorized access to facilities, the IR team coordinates with the physical security team to investigate and respond to the incident. This collaboration ensures that both digital and physical threats are addressed.
Threat Intelligence Analyst Roles and Responsibilities

The Threat Intelligence Analyst is a critical role within the SOC, focusing on proactively identifying, analyzing, and understanding threats to an organization’s digital assets. This involves collecting and processing information from various sources to provide actionable intelligence that informs security decisions and improves the overall security posture. They act as the bridge between raw threat data and the actions needed to defend against those threats.
Proactive Threat Hunting with Threat Intelligence
Threat Intelligence Analysts play a crucial role in proactive threat hunting. This involves actively searching for malicious activity within an organization’s network and systems, even before an alert is triggered. This proactive approach is significantly different from reactive incident response.The process involves several key steps:
- Developing hypotheses: Based on threat intelligence, analysts formulate hypotheses about potential threats that may be targeting the organization. For example, they might hypothesize that a specific malware family, known to be targeting similar organizations, is present.
- Identifying indicators of compromise (IOCs): The analyst uses threat intelligence to identify IOCs associated with the hypothesized threat. These IOCs could include specific IP addresses, domain names, file hashes, or registry keys.
- Searching for IOCs: Using security tools like SIEM (Security Information and Event Management) systems, endpoint detection and response (EDR) solutions, and network monitoring tools, the analyst searches for the identified IOCs within the organization’s environment.
- Analyzing findings: When IOCs are detected, the analyst investigates the context surrounding the detection. This involves examining logs, network traffic, and other relevant data to determine if the activity is malicious.
- Providing recommendations: Based on their findings, the analyst provides recommendations to other SOC team members, such as incident responders, on how to contain and eradicate the threat. They might also recommend changes to security controls to prevent future attacks.
Threat Intelligence Feeds into Incident Detection and Prevention
Threat intelligence significantly improves incident detection and prevention capabilities. By understanding the threat landscape, organizations can proactively prepare for attacks and respond more effectively when incidents occur.This integration happens in several ways:
- Improved detection rules: Threat intelligence is used to create and refine detection rules within security tools like SIEM systems and intrusion detection systems (IDS). These rules help to identify malicious activity based on known IOCs and tactics, techniques, and procedures (TTPs). For instance, if a threat intelligence feed reports a new phishing campaign using a specific subject line, the analyst can create a rule to detect emails with that subject line.
- Enhanced security controls: Threat intelligence informs the configuration and deployment of security controls. This might include blocking malicious IP addresses at the firewall, blacklisting malicious domains in web proxies, or deploying endpoint protection software that can detect and block known malware.
- Prioritized incident response: Threat intelligence helps to prioritize incident response efforts. When an incident is detected, the analyst can use threat intelligence to assess the severity of the threat and the potential impact on the organization. This allows the incident response team to focus on the most critical incidents first.
- Vulnerability management: Threat intelligence provides insights into vulnerabilities being actively exploited by attackers. This information helps organizations prioritize patching efforts and reduce their attack surface. For example, if threat intelligence reveals that a specific vulnerability in a widely used software is being actively exploited, the organization can prioritize patching that software.
Sources of Threat Intelligence
Threat intelligence is gathered from a wide variety of sources. Analysts must be adept at assessing the credibility and relevance of each source. The following are some common sources:
- Open Source Intelligence (OSINT): This includes publicly available information from various sources.
- News articles and security blogs: These sources provide information about emerging threats, vulnerabilities, and attack campaigns.
- Social media: Platforms like Twitter and Reddit can be used to identify and track threat actors, emerging trends, and discussions about security incidents.
- Vulnerability databases: Websites like the National Vulnerability Database (NVD) provide information about known vulnerabilities and their associated risks.
- Publicly available malware repositories: These repositories contain samples of malware that can be analyzed to understand their behavior and identify IOCs.
- Commercial Threat Intelligence Feeds: These are subscription-based services that provide curated threat intelligence data.
- Threat data feeds: These feeds provide real-time information about malicious IP addresses, domain names, file hashes, and other IOCs.
- Reports and analysis: Commercial providers often publish detailed reports and analysis on threat actors, attack campaigns, and emerging threats.
- Vulnerability intelligence: These services provide information about known vulnerabilities, including their severity, exploitation status, and recommended mitigation steps.
- Internal Intelligence: This includes information gathered from within the organization.
- Security logs and alerts: Analyzing security logs and alerts can reveal patterns of malicious activity and identify potential threats.
- Incident response reports: Reports from previous incidents can provide valuable insights into the tactics, techniques, and procedures (TTPs) used by attackers.
- Vulnerability assessments and penetration tests: These activities can identify vulnerabilities in the organization’s systems and networks.
- Industry-Specific Information Sharing and Analysis Centers (ISACs): These organizations facilitate the sharing of threat intelligence and best practices among members within a specific industry.
- Sharing threat data: ISACs provide a platform for members to share information about threats and vulnerabilities.
- Developing best practices: ISACs develop and share best practices for cybersecurity within their respective industries.
- Facilitating collaboration: ISACs facilitate collaboration among members to address common cybersecurity challenges.
SOC Manager/Lead Roles and Responsibilities
The SOC Manager/Lead plays a pivotal role in the success of a Security Operations Center. They are responsible for the overall management, strategic direction, and operational effectiveness of the SOC. Their duties encompass leadership, policy creation, performance monitoring, and ensuring the SOC aligns with the organization’s security goals.
Management and Leadership Responsibilities of a SOC Manager
The SOC Manager’s primary focus is on guiding and supporting the SOC team, ensuring they have the resources and training necessary to effectively detect, analyze, and respond to security incidents. They also act as a key liaison between the SOC and other departments within the organization.
- Team Leadership and Mentorship: The SOC Manager provides leadership, guidance, and mentorship to the SOC team. This includes fostering a positive and collaborative work environment, promoting professional development, and conducting performance evaluations. They identify training needs and ensure team members have the necessary skills to perform their duties.
- Strategic Planning and Goal Setting: They are responsible for developing and implementing the SOC’s strategic plan, aligning it with the organization’s overall security objectives. This involves setting goals, defining key performance indicators (KPIs), and monitoring progress. The SOC Manager also identifies and mitigates risks to the SOC’s operations.
- Resource Management: The SOC Manager manages the SOC’s budget, resources, and infrastructure. This includes procuring and maintaining security tools and technologies, ensuring adequate staffing levels, and managing vendor relationships. They also ensure the SOC has the necessary tools and technologies to perform its functions effectively.
- Incident Management and Escalation: While the Incident Response Team handles the initial stages of incident response, the SOC Manager oversees the overall incident management process. They ensure that incidents are properly escalated, investigated, and resolved, and that lessons learned are incorporated into future security strategies.
- Communication and Reporting: The SOC Manager is responsible for communicating with stakeholders, including executive management, IT departments, and other relevant teams. They provide regular reports on SOC activities, including key metrics, incident summaries, and recommendations for improvement. They ensure stakeholders are informed about security threats and vulnerabilities.
Establishing and Maintaining SOC Policies and Procedures
Establishing and maintaining comprehensive policies and procedures is crucial for ensuring consistency, efficiency, and compliance within the SOC. These documents provide a framework for how the SOC operates and responds to security incidents.
- Policy Development: The SOC Manager is responsible for developing and maintaining a suite of policies that govern the SOC’s operations. These policies should cover areas such as incident response, data handling, access control, and acceptable use. The policies should be aligned with industry best practices and regulatory requirements (e.g., GDPR, HIPAA).
- Procedure Creation: Detailed procedures provide step-by-step instructions for specific tasks, such as incident detection, analysis, and response. The SOC Manager oversees the creation and maintenance of these procedures, ensuring they are up-to-date, accurate, and easy to follow. Procedures should be regularly reviewed and updated to reflect changes in the threat landscape or organizational policies.
- Documentation and Version Control: All policies and procedures must be thoroughly documented and version-controlled. This ensures that the SOC team has access to the latest information and that changes are tracked and documented. Effective documentation is essential for training new team members and for maintaining consistency across the SOC.
- Training and Awareness: The SOC Manager ensures that all team members are properly trained on the policies and procedures. This includes providing regular training sessions, conducting drills, and promoting awareness of security best practices. Training should be tailored to the specific roles and responsibilities within the SOC.
- Regular Review and Updates: Policies and procedures should be regularly reviewed and updated to reflect changes in the threat landscape, organizational policies, and regulatory requirements. The SOC Manager is responsible for leading this review process, soliciting feedback from the SOC team, and incorporating necessary changes.
Performance Metrics and Reporting in a SOC Environment
Performance metrics and reporting are essential for measuring the effectiveness of the SOC, identifying areas for improvement, and demonstrating the value of the SOC to the organization.
- Key Performance Indicators (KPIs): The SOC Manager defines and tracks key performance indicators (KPIs) to measure the SOC’s performance. Examples of KPIs include:
- Mean Time to Detect (MTTD): The average time it takes to detect a security incident.
- Mean Time to Respond (MTTR): The average time it takes to respond to a security incident.
- Number of Incidents Detected and Resolved: The total number of security incidents detected and resolved within a specific timeframe.
- False Positive Rate: The percentage of alerts that are incorrectly identified as security incidents.
- Alert Volume: The total number of alerts generated by security tools.
These metrics provide a clear picture of the SOC’s efficiency and effectiveness.
- Reporting and Analysis: The SOC Manager is responsible for generating regular reports on SOC activities, including KPIs, incident summaries, and trends. These reports should be presented to relevant stakeholders, including executive management and IT departments. Analysis of the data helps identify areas for improvement and inform future security strategies.
- Dashboarding and Visualization: Using dashboards and data visualization tools can help present complex security data in an easy-to-understand format. The SOC Manager can use dashboards to track real-time metrics, identify trends, and monitor the overall health of the SOC.
- Continuous Improvement: The data collected through performance metrics should be used to drive continuous improvement within the SOC. The SOC Manager uses the insights from the data to identify areas for improvement, implement changes, and measure the impact of those changes. This includes optimizing security tools, refining procedures, and providing additional training.
- Compliance and Auditing: The SOC Manager ensures that the SOC’s activities are compliant with relevant regulations and standards. This includes conducting regular audits, documenting security controls, and preparing for compliance assessments.
Security Engineer Roles and Responsibilities
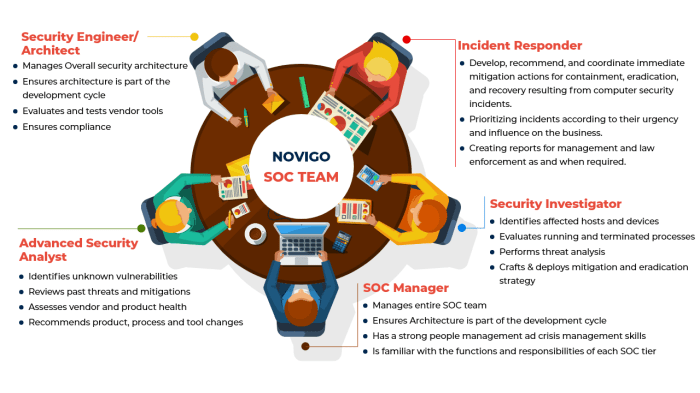
Security Engineers are critical to the effective operation of a Security Operations Center (SOC). They bridge the gap between security strategy and technical implementation, ensuring that security tools and infrastructure are properly configured, maintained, and optimized to detect and respond to threats. Their expertise allows the SOC to operate efficiently and effectively, minimizing the impact of security incidents.
Supporting SOC Operations
Security Engineers provide essential support to the SOC, ensuring the tools and systems used by the team are functioning optimally. This involves a wide range of activities that directly impact the SOC’s ability to identify, analyze, and respond to security incidents.
- Tool Configuration and Maintenance: Security Engineers are responsible for the initial configuration and ongoing maintenance of security tools, including Security Information and Event Management (SIEM) systems, intrusion detection and prevention systems (IDS/IPS), endpoint detection and response (EDR) solutions, vulnerability scanners, and security orchestration, automation, and response (SOAR) platforms. This includes defining rules, creating dashboards, and tuning alerts to ensure effective threat detection.
- Automation and Scripting: They automate repetitive tasks and workflows within the SOC. This might involve scripting to automate incident response procedures, data enrichment, or system administration tasks, freeing up analysts to focus on more complex investigations.
- System Integration: Security Engineers integrate various security tools and systems to ensure seamless data flow and interoperability. This includes connecting SIEM systems with other security tools, integrating threat intelligence feeds, and configuring data connectors to collect logs from diverse sources.
- Vulnerability Management: They support vulnerability management processes by configuring and managing vulnerability scanning tools, analyzing scan results, and assisting in the remediation of identified vulnerabilities. This helps to reduce the attack surface and improve the overall security posture.
- Incident Response Support: During security incidents, Security Engineers provide technical expertise and support to the incident response team. This might involve assisting with malware analysis, forensic investigations, or system recovery efforts.
- Performance Monitoring and Optimization: They monitor the performance of security tools and systems, identifying bottlenecks and areas for optimization. This ensures that the SOC’s tools can handle the volume of data and events without impacting performance.
Configuring and Maintaining Security Tools
The configuration and maintenance of security tools is a core responsibility of Security Engineers. This involves a detailed understanding of each tool’s capabilities and how they can be effectively deployed to meet the SOC’s needs.
- SIEM Configuration: Configuring SIEM systems involves defining data sources, creating parsing rules, developing correlation rules, and building dashboards. For example, a Security Engineer might configure a SIEM like Splunk or QRadar to collect logs from firewalls, intrusion detection systems, and servers. They would then create rules to detect suspicious activity, such as failed login attempts or unusual network traffic patterns.
- IDS/IPS Tuning: Tuning intrusion detection and prevention systems involves adjusting rules and signatures to minimize false positives and false negatives. A Security Engineer might analyze the logs from an IDS/IPS like Snort or Suricata to identify legitimate traffic that is being flagged as malicious. They would then adjust the rules to reduce the number of false positives while still maintaining effective threat detection.
- EDR Implementation: Implementing EDR solutions involves installing agents on endpoints, configuring policies, and integrating the EDR tool with the SIEM. A Security Engineer might deploy an EDR solution like CrowdStrike or SentinelOne across the organization’s endpoints. They would then configure policies to detect and respond to malicious activity, such as malware infections or unauthorized access attempts.
- Vulnerability Scanning: Setting up vulnerability scanning involves configuring the scanning tool, defining scan schedules, and analyzing the results. A Security Engineer might use a vulnerability scanner like Nessus or OpenVAS to scan the organization’s network and systems for vulnerabilities. They would then analyze the scan results to identify and prioritize vulnerabilities, and work with other teams to remediate them.
- SOAR Automation: Implementing SOAR platforms involves creating automated workflows for incident response and threat hunting. A Security Engineer might use a SOAR platform like Demisto or Swimlane to automate tasks such as malware analysis, phishing email triage, and vulnerability assessment.
Collaboration with Other SOC Teams
Security Engineers work closely with other teams within the SOC and across the organization to ensure effective security operations. Collaboration is key to a cohesive and efficient security posture.
- Security Analysts: They provide technical support to Security Analysts, helping them to understand and interpret security alerts and incidents. This includes providing guidance on how to use security tools, troubleshooting technical issues, and assisting with investigations. For example, a Security Engineer might help an analyst to analyze a suspicious file by providing malware analysis tools or explaining how a particular network protocol works.
- Incident Response Team: They collaborate with the Incident Response Team during security incidents, providing technical expertise and support. This includes assisting with forensic investigations, malware analysis, and system recovery efforts. For instance, they might help the incident response team to identify the root cause of a breach, contain the damage, and restore affected systems.
- Threat Intelligence Team: They work with the Threat Intelligence Team to integrate threat intelligence feeds into security tools and systems. This helps to improve threat detection and response capabilities. For example, a Security Engineer might configure the SIEM to ingest threat intelligence feeds from various sources, such as the MISP (Malware Information Sharing Project) or commercial threat intelligence providers.
- Network Engineers: They collaborate with Network Engineers to ensure that network infrastructure is secure and that security tools are properly integrated. This includes working together on firewall rules, network segmentation, and intrusion detection systems.
- System Administrators: They work with System Administrators to ensure that systems are properly configured and patched, and that security best practices are followed. This includes working together on vulnerability remediation, system hardening, and access control.
Tools and Technologies Used in a SOC
A Security Operations Center (SOC) relies heavily on a diverse set of tools and technologies to effectively monitor, detect, analyze, and respond to security threats. These tools automate and streamline various security tasks, enabling SOC teams to work efficiently and proactively. The selection and implementation of these tools are critical for the overall effectiveness of the SOC.
Categories of Security Tools
SOCs employ a wide array of security tools, each designed to address specific aspects of cybersecurity. These tools can be broadly categorized based on their primary function. Understanding these categories helps in organizing and managing the tools effectively.
- Security Information and Event Management (SIEM): These systems collect, analyze, and correlate security logs from various sources to provide real-time visibility into security events.
- Endpoint Detection and Response (EDR): EDR tools monitor endpoints (e.g., laptops, servers) for malicious activities and provide capabilities for threat detection, investigation, and response.
- Network Security Tools: These tools focus on securing network traffic and infrastructure. They include firewalls, intrusion detection/prevention systems (IDS/IPS), and network monitoring solutions.
- Vulnerability Management Tools: These tools scan systems and applications for vulnerabilities, providing insights into security weaknesses and enabling remediation efforts.
- Threat Intelligence Platforms (TIP): TIPs collect, analyze, and disseminate threat intelligence data, helping SOC teams understand the threat landscape and proactively defend against emerging threats.
- Security Orchestration, Automation, and Response (SOAR): SOAR platforms automate security tasks, such as incident response, threat hunting, and vulnerability management, to improve efficiency and reduce response times.
- Data Loss Prevention (DLP): DLP tools monitor and prevent sensitive data from leaving the organization’s control.
Comparing SIEM Systems
Security Information and Event Management (SIEM) systems are at the heart of many SOC operations. They aggregate log data from various sources, perform analysis, and generate alerts. While all SIEMs share a common goal, they differ in their features, scalability, and ease of use. Evaluating these differences is crucial when selecting a SIEM solution.
- Log Collection and Storage: SIEMs vary in their ability to collect and store logs from different sources, including servers, network devices, and applications. Some SIEMs support a wider range of log formats and have greater storage capacity.
- Event Correlation and Analysis: SIEMs use correlation rules and algorithms to identify security incidents from raw log data. The sophistication of these rules and the accuracy of analysis are key differentiators.
- Alerting and Reporting: SIEMs generate alerts based on predefined rules and provide reporting capabilities to track security incidents and overall security posture. The customization options for alerts and reports vary between systems.
- User Interface and Usability: The user interface and ease of use are important factors in SIEM selection. A well-designed interface allows analysts to quickly investigate incidents and perform their tasks.
- Scalability and Performance: SIEMs must be able to handle large volumes of log data and maintain performance. Scalability is particularly important for organizations with large IT infrastructures.
- Integration and API Support: SIEMs often integrate with other security tools and use APIs to share data and automate tasks. The level of integration support can impact the overall effectiveness of the SOC.
Tools, Purpose, and Examples
The following table details various types of tools used in a SOC, along with their primary purpose and examples of specific tools. This provides a comprehensive overview of the technologies used to defend against cyber threats.
| Tool Type | Purpose | Examples |
|---|---|---|
| SIEM | Collects, analyzes, and correlates security logs to detect and respond to threats. | Splunk Enterprise Security, IBM QRadar, Microsoft Sentinel, Elastic Security |
| EDR | Monitors endpoints for malicious activity and provides threat detection, investigation, and response capabilities. | CrowdStrike Falcon, Carbon Black, Microsoft Defender for Endpoint, SentinelOne |
| Firewall | Controls network traffic based on predefined security rules. | Cisco Firepower, Palo Alto Networks, Fortinet FortiGate |
| IDS/IPS | Detects and prevents malicious network activity. | Snort, Suricata, Cisco Firepower IPS, Palo Alto Networks IPS |
| Vulnerability Scanner | Identifies vulnerabilities in systems and applications. | Nessus, OpenVAS, Rapid7 InsightVM, Qualys Vulnerability Management |
| Threat Intelligence Platform (TIP) | Collects, analyzes, and disseminates threat intelligence data. | Anomali ThreatStream, Recorded Future, ThreatConnect, MISP |
| SOAR | Automates security tasks, such as incident response and threat hunting. | Splunk Phantom, Demisto (now Palo Alto Networks Cortex XSOAR), Swimlane, Rapid7 InsightConnect |
| Network Monitoring Tools | Monitors network traffic and performance. | Wireshark, SolarWinds Network Performance Monitor, PRTG Network Monitor |
| Data Loss Prevention (DLP) | Monitors and prevents sensitive data from leaving the organization. | McAfee DLP, Symantec DLP, Digital Guardian, Forcepoint DLP |
| Security Automation Tools | Automates repetitive security tasks. | Ansible, Chef, Puppet |
Communication and Collaboration within a SOC

Effective communication and collaboration are the cornerstones of a successful Security Operations Center (SOC). A well-oiled SOC operates on the principles of clear, concise, and timely information exchange, both internally and externally. This section will explore the critical importance of establishing robust communication channels, leveraging collaborative tools, and maintaining comprehensive documentation to ensure efficient incident handling, proactive threat hunting, and overall security posture.
Importance of Clear Communication Channels
Establishing clear communication channels is paramount for a SOC to function effectively. Ambiguity, delays, or misunderstandings can lead to critical errors, missed threats, and prolonged incident response times. A structured approach to communication, encompassing both formal and informal channels, is vital for maintaining situational awareness and ensuring everyone is informed.
- Incident Escalation Protocols: Predefined escalation paths are essential for ensuring that critical incidents are brought to the attention of the appropriate personnel without delay. These protocols should clearly define who to contact, when, and how, based on the severity and type of incident. For instance, a high-priority malware outbreak might trigger immediate notification of the SOC Manager, the Incident Response Team Lead, and potentially the Chief Information Security Officer (CISO).
- Regular Team Meetings: Scheduled meetings, such as daily stand-ups or weekly team meetings, provide opportunities to share updates, discuss ongoing investigations, and coordinate activities. These meetings help maintain situational awareness and foster a sense of teamwork. The SOC team can review recent alerts, discuss any challenges, and plan for upcoming tasks during the meetings.
- Defined Communication Roles: Each team member should understand their communication responsibilities. This includes knowing who to contact for specific types of issues, how to document communications, and the preferred communication methods for different situations. Clear role definitions prevent confusion and ensure accountability.
- Internal Communication Channels: Secure and reliable internal communication channels are crucial. These channels can include instant messaging platforms, email, and dedicated communication tools for incident response.
- External Communication Protocols: Protocols should be in place for communicating with external stakeholders, such as vendors, law enforcement, and affected parties. These protocols should cover aspects like information sharing, reporting requirements, and the chain of custody for evidence.
Tools and Methods for Effective Collaboration
Utilizing the right tools and methods can significantly enhance collaboration within a SOC, fostering a more efficient and effective security posture. The choice of tools should align with the specific needs and workflows of the SOC.
- Security Information and Event Management (SIEM) Systems: SIEM systems act as a central hub for security data, providing a platform for collaboration by allowing analysts to share alerts, investigations, and findings. Many SIEM platforms include built-in collaboration features, such as the ability to add comments, assign tasks, and track the progress of investigations.
- Incident Response Platforms (IRP): IRPs streamline the incident response process by providing a centralized platform for managing incidents, tracking progress, and coordinating activities. These platforms often include features such as workflow automation, collaboration tools, and reporting capabilities.
- Collaboration Platforms (e.g., Slack, Microsoft Teams): Instant messaging platforms facilitate real-time communication and information sharing within the SOC. These platforms enable quick discussions, file sharing, and the creation of dedicated channels for specific projects or incidents.
- Ticketing Systems (e.g., ServiceNow, Jira): Ticketing systems are essential for tracking and managing security incidents, tasks, and requests. They provide a centralized repository for all relevant information, allowing teams to track progress, assign responsibilities, and ensure accountability.
- Version Control Systems (e.g., Git): Version control systems are invaluable for managing and collaborating on code, configurations, and documentation. They allow teams to track changes, revert to previous versions, and collaborate on projects without conflicts.
- Threat Intelligence Platforms (TIPs): TIPs facilitate collaboration by providing a centralized repository for threat intelligence data. Analysts can share information, collaborate on investigations, and stay informed about the latest threats.
Role of Documentation in Ensuring Consistent SOC Operations
Comprehensive and up-to-date documentation is a cornerstone of consistent and effective SOC operations. Documentation provides a common reference point, reduces ambiguity, and ensures that processes are followed consistently, even when personnel changes occur. It also supports training, auditing, and compliance efforts.
- Standard Operating Procedures (SOPs): SOPs are detailed, step-by-step instructions for performing specific tasks, such as incident response, malware analysis, and vulnerability assessment. They ensure consistency and repeatability in SOC operations.
- Runbooks: Runbooks are similar to SOPs but often focus on automated or semi-automated procedures. They provide clear instructions for responding to specific types of incidents or alerts, often including scripts or commands to execute.
- Incident Response Plans (IRPs): IRPs Artikel the processes and procedures for handling security incidents, including roles and responsibilities, communication protocols, and escalation procedures. A well-defined IRP helps to minimize the impact of incidents and ensure a swift and effective response.
- Knowledge Base: A knowledge base is a central repository for information about known issues, vulnerabilities, and solutions. It helps analysts quickly find answers to common problems and reduces the need for repetitive research.
- Asset Inventory: A detailed asset inventory provides a comprehensive list of all IT assets, including hardware, software, and network devices. This information is crucial for vulnerability management, incident response, and compliance efforts.
- Configuration Management Database (CMDB): A CMDB is a database that stores information about IT assets, their configurations, and their relationships. It provides a centralized view of the IT environment, which is essential for managing change, troubleshooting issues, and ensuring compliance.
- Documentation Updates: Documentation must be regularly reviewed and updated to reflect changes in the environment, new threats, and updated procedures. Regular reviews and updates ensure that the documentation remains accurate and relevant.
Last Word
In conclusion, understanding the roles and responsibilities within a SOC is critical for any organization seeking robust cybersecurity. By recognizing the importance of each team member, the tools they utilize, and the collaborative spirit that drives them, businesses can build a resilient defense against the ever-present threat landscape. Investing in a well-structured SOC, equipped with the right talent and technology, is an investment in the future of your organization’s security and success.
FAQ Corner
What is the primary goal of a SOC?
The primary goal of a SOC is to protect an organization’s digital assets by detecting, analyzing, and responding to security incidents, ultimately minimizing their impact.
What are the key differences between a Level 1 and Level 2 Security Analyst?
Level 1 analysts typically handle initial triage, alert investigation, and escalation, while Level 2 analysts possess deeper technical expertise, performing more in-depth analysis and incident response.
How does a SOC contribute to proactive threat hunting?
SOCs utilize threat intelligence and advanced analytics to proactively search for hidden threats within the network, identifying vulnerabilities and preventing potential attacks before they occur.
What is the role of a SIEM in a SOC?
A SIEM (Security Information and Event Management) system aggregates and analyzes security logs from various sources, providing real-time visibility into security events and enabling faster incident detection and response.
Why is documentation important in a SOC?
Documentation ensures consistency in operations, provides a reference for incident response procedures, and facilitates knowledge sharing among team members, contributing to overall efficiency and effectiveness.